Crook's Office365 Infiltration Nets Millions: FBI Investigation

Table of Contents
The Modus Operandi: How Crooks Infiltrated Office365
The perpetrators behind this widespread Office365 security breach employed a multi-pronged approach, leveraging various methods to gain unauthorized access to victims' accounts and data. Their sophisticated tactics demonstrate a clear understanding of common Office365 vulnerabilities and user behaviors. These methods include:
- Sophisticated Phishing Attacks: Victims received highly convincing phishing emails meticulously crafted to mimic legitimate communications from trusted sources. These emails often contained malicious links or attachments designed to install malware or steal credentials.
- Credential Stuffing: The perpetrators used lists of stolen usernames and passwords obtained from previous data breaches to attempt logins to Office365 accounts. Weak or reused passwords made many accounts vulnerable to this technique.
- Malware Infection: Once initial access was gained, malware was often deployed to maintain persistent access to the compromised accounts and systems. This allowed for data exfiltration and continued malicious activity.
- Exploiting Third-Party Application Vulnerabilities: The attackers exploited vulnerabilities in third-party applications integrated with Office365, gaining access through less-secured points of entry.
The impact of these methods was significant, leading to data exfiltration, account hijacking, and disruption of business operations. The stolen data included sensitive financial information, confidential business documents, and intellectual property, resulting in substantial financial losses and reputational damage for the victims.
The Scale of the Damage: Financial Losses and Data Breaches
The financial losses incurred by victims of this Office365 security breach are staggering, amounting to millions of dollars in direct costs and indirect consequences. The data breach compromised a wide range of sensitive information, including:
- Financial Information: Bank account details, credit card numbers, and other sensitive financial data were exposed.
- Sensitive Business Data: Confidential business plans, customer lists, and intellectual property were stolen, impacting competitive advantage and potentially leading to legal repercussions.
- Employee Data: Personally identifiable information (PII) of employees was compromised, raising privacy concerns and potential legal liabilities.
The long-term consequences for affected businesses and individuals are far-reaching. Beyond the immediate financial losses, victims face:
- Reputational Damage: Data breaches can severely damage an organization's reputation and trust among customers and partners.
- Legal Ramifications: Organizations may face legal actions from affected individuals and regulatory fines for non-compliance with data protection regulations.
- Increased Cybersecurity Costs: The costs associated with incident response, data recovery, and improved security measures can be substantial.
The FBI's Response and Ongoing Investigation
The FBI has launched a full-scale investigation into this significant Office365 security breach. Their response includes:
- Working with affected organizations: The FBI is collaborating closely with victim organizations to mitigate the damage and gather evidence.
- Pursuing criminal charges: The FBI is actively pursuing criminal charges against the suspected perpetrators, working internationally to bring them to justice.
- Issuing public warnings and security advisories: The FBI has issued public warnings and security advisories, highlighting the threat and providing guidance on protecting against similar attacks. These advisories emphasize the importance of robust Office365 security practices.
The ongoing investigation is complex and extensive, but the FBI’s proactive response demonstrates a commitment to combating cybercrime and protecting businesses and individuals from these threats. The FBI’s actions serve as a stark reminder of the seriousness of such breaches and the importance of strong cybersecurity measures.
Protecting Your Organization from Similar Office365 Infiltration Attempts
Preventing similar Office365 infiltration attempts requires a multi-layered approach to security. Proactive measures are crucial to safeguarding your organization's data and reputation. Consider these essential steps:
- Implement Multi-Factor Authentication (MFA): MFA adds an extra layer of security, making it significantly harder for attackers to access accounts even if they obtain usernames and passwords.
- Regularly Update Software and Patches: Keep all software, including Office365 applications and operating systems, up-to-date with the latest security patches to mitigate known vulnerabilities.
- Conduct Employee Security Awareness Training: Educate employees about phishing scams, social engineering tactics, and best practices for password security.
- Enforce Strong, Unique Passwords: Implement a strong password policy that mandates complex, unique passwords for all accounts.
- Monitor Account Activity for Suspicious Behavior: Regularly monitor account activity for any unusual login attempts or suspicious behavior. Set up alerts for unauthorized access attempts.
- Employ Advanced Threat Protection Tools: Invest in advanced threat protection tools that can detect and prevent sophisticated attacks.
By implementing these proactive security measures, organizations can significantly reduce their risk of falling victim to similar Office365 security breaches.
Conclusion: Learning from the Crook's Office365 Infiltration
The FBI investigation into this massive Office365 infiltration highlights the significant financial losses and data breaches that can result from inadequate cybersecurity practices. The scale of this breach underscores the critical importance of proactive security measures to prevent similar incidents. The perpetrators' sophisticated methods demonstrate the need for comprehensive security strategies that address multiple attack vectors.
Protect your organization from becoming the next victim of an Office365 infiltration. Implement robust Office365 security measures today! Don't wait for a devastating data breach to prioritize your cybersecurity. Take action now to protect your sensitive data, maintain your reputation, and avoid costly financial repercussions. Improve your Office365 security posture and secure your future.

Featured Posts
-
 Exclusive Offer 1 500 Flight Credit For Agents Selling Paul Gauguin Cruises Via Ponant
May 02, 2025
Exclusive Offer 1 500 Flight Credit For Agents Selling Paul Gauguin Cruises Via Ponant
May 02, 2025 -
 V Sogde Obsudili Mery Borby S Torgovley Lyudmi Itogi Vstrechi
May 02, 2025
V Sogde Obsudili Mery Borby S Torgovley Lyudmi Itogi Vstrechi
May 02, 2025 -
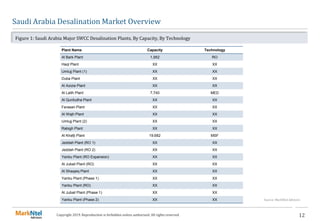 Analyzing The Effects Of Saudi Arabias Revised Abs Market Regulations
May 02, 2025
Analyzing The Effects Of Saudi Arabias Revised Abs Market Regulations
May 02, 2025 -
 Is Doctor Who Taking A Break Russell T Davies Offers Clues
May 02, 2025
Is Doctor Who Taking A Break Russell T Davies Offers Clues
May 02, 2025 -
 England Vs Spain Tv Channel Kick Off Time And How To Watch The Lionesses
May 02, 2025
England Vs Spain Tv Channel Kick Off Time And How To Watch The Lionesses
May 02, 2025
Latest Posts
-
 I Diafthora Stis Poleodomies Proklisi Gia Tin Epanidrysi Enos Dikaioy Kratoys
May 03, 2025
I Diafthora Stis Poleodomies Proklisi Gia Tin Epanidrysi Enos Dikaioy Kratoys
May 03, 2025 -
 Lakazet S 157 Gola Lion Se Priblizhava Do Vrkha Vv Frantsiya
May 03, 2025
Lakazet S 157 Gola Lion Se Priblizhava Do Vrkha Vv Frantsiya
May 03, 2025 -
 Rekordt Na Lakazet 157 Gola I Borbata Za Vtoroto Myasto V Liga 1
May 03, 2025
Rekordt Na Lakazet 157 Gola I Borbata Za Vtoroto Myasto V Liga 1
May 03, 2025 -
 157 I Gol Za Lakazet Lion Napn Za Vtoroto Myasto Vv Frantsiya
May 03, 2025
157 I Gol Za Lakazet Lion Napn Za Vtoroto Myasto Vv Frantsiya
May 03, 2025 -
 Lakazet Izprevarva Papen Lion E Blizo Do Vtoroto Myasto
May 03, 2025
Lakazet Izprevarva Papen Lion E Blizo Do Vtoroto Myasto
May 03, 2025
