Cybercriminal Nets Millions Through Executive Office365 Account Compromise
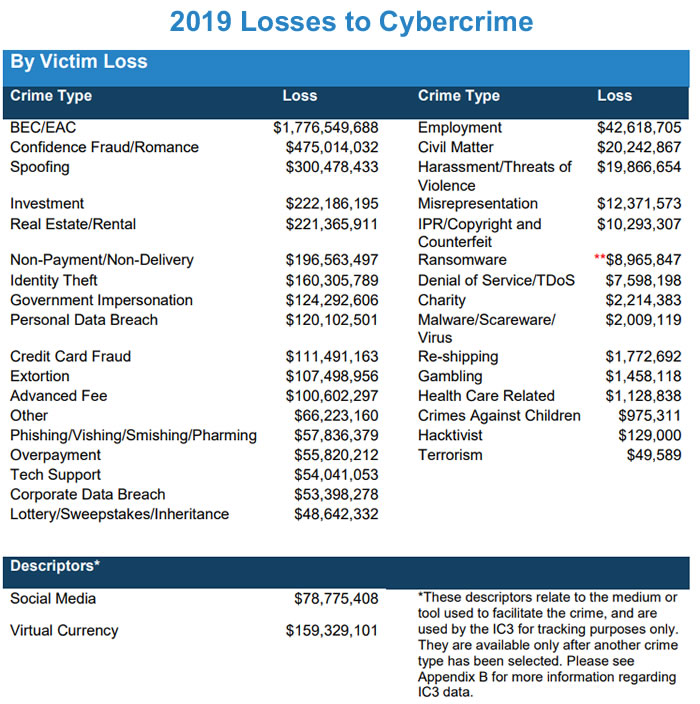
Table of Contents
The Anatomy of the Office365 Executive Account Compromise
This successful cyberattack underscores the need for robust security protocols. Let's examine the likely steps taken by the attacker:
Phishing and Social Engineering
The most probable initial vector was a sophisticated phishing attack combined with social engineering. Attackers rarely rely on simple, easily-detected phishing attempts.
- Examples of sophisticated phishing emails: These might mimic urgent requests from a client, a critical financial alert seemingly from the bank, or even impersonate a trusted colleague. CEO fraud, where emails appear to originate from the CEO, is particularly effective.
- Use of brand impersonation: Attackers create convincingly fake websites and emails mirroring legitimate company branding to deceive victims.
- Exploiting urgency and fear: Phishing emails often create a sense of urgency or fear, pressuring the recipient into acting quickly without critically evaluating the message. This bypasses rational security thinking.
Attackers meticulously craft these emails, often utilizing advanced techniques like spear phishing (targeting specific individuals) and whaling (targeting high-value individuals like executives). They leverage publicly available information to personalize the emails, making them even more believable and increasing the chances of success.
Exploiting Weak Passwords and Lack of MFA
Even the most sophisticated phishing email would likely fail if robust security measures were in place. This attack highlights the critical role of weak passwords and the absence of multi-factor authentication (MFA).
- Statistics on password breaches: Millions of accounts are compromised annually due to weak or reused passwords.
- The effectiveness of MFA in preventing attacks: MFA adds an extra layer of security, significantly reducing the risk of unauthorized access, even if passwords are compromised.
- Examples of strong password practices: Utilizing long, complex passwords, incorporating a mix of uppercase and lowercase letters, numbers, and symbols, and regularly changing passwords are crucial practices.
The lack of MFA allowed the attacker to gain access to the executive's account even after obtaining the password through phishing. This underscores the absolute necessity of implementing MFA across all accounts, especially for those with high levels of access.
Internal Vulbilities and Insider Threats
While an external attack is highly likely, the possibility of internal vulnerabilities or insider threats cannot be ruled out.
- Examples of negligent employees: Unintentional actions, such as clicking on malicious links or failing to report suspicious activity, can facilitate attacks.
- Compromised internal systems: Weak internal security within the company's network could have allowed the attacker easier access.
- Social engineering targeting employees: Attackers may have targeted employees other than the executive to gain initial access to the network before focusing on the executive account.
Understanding the potential for internal weaknesses is vital. Regular security audits and employee training are essential preventative measures.
The Financial Ramifications of the Breach
The consequences of this Office365 executive account compromise extend far beyond the immediate financial loss.
Direct Financial Losses
The millions stolen represent a significant blow, but the actual financial damage could be much higher.
- Specific examples of financial fraud: The attacker likely used the compromised account to authorize fraudulent wire transfers, approve fake invoices, or manipulate financial reporting.
- The process used to transfer funds: The attacker may have used the compromised email to initiate wire transfers to offshore accounts or manipulated accounting systems to mask the fraudulent transactions.
The immediate financial losses are substantial, impacting the company's profitability and potentially leading to liquidity problems.
Reputational Damage and Legal Consequences
Beyond the direct financial impact, the breach carries significant reputational damage and potential legal repercussions.
- Loss of customer trust: A data breach can severely damage a company's reputation, leading to a loss of customer trust and potentially impacting future business.
- Potential lawsuits: Affected parties might file lawsuits against the company for negligence and financial losses.
- Regulatory fines: Non-compliance with data protection regulations can result in substantial fines.
The long-term effects on the company's image and its ability to attract investors and clients can be devastating.
Best Practices for Preventing Office365 Executive Account Compromise
Protecting against these attacks demands a multi-layered security approach.
Implementing Robust MFA
Multi-factor authentication (MFA) is non-negotiable.
- Different types of MFA: Options include one-time passwords (OTP) via SMS or authenticator apps, biometric authentication (fingerprint or facial recognition), and security keys.
- Benefits of using MFA: MFA significantly reduces the likelihood of account compromise, even if passwords are stolen or guessed.
MFA provides an essential layer of security, making it exponentially harder for attackers to access accounts even if they obtain usernames and passwords.
Security Awareness Training
Investing in comprehensive security awareness training is paramount.
- Regular phishing simulations: Simulating phishing attacks helps train employees to identify and report suspicious emails.
- Training modules on recognizing suspicious emails: Training should cover various phishing techniques and social engineering tactics.
- Reporting procedures: Clear procedures for reporting suspicious emails and security incidents must be established and consistently enforced.
Regular training empowers employees to become the first line of defense against phishing attacks.
Advanced Threat Protection
Advanced threat protection tools are crucial for identifying and neutralizing sophisticated attacks.
- Examples of advanced threat protection solutions: Email filtering, sandboxing (analyzing emails in a safe environment before delivery), and URL analysis tools.
- Their benefits: These solutions can detect and block malicious emails and attachments that might bypass basic security measures.
Advanced threat protection provides an additional layer of defense beyond traditional email security measures.
Regular Security Audits and Penetration Testing
Proactive security measures are crucial.
- The importance of periodic security audits and penetration testing: Regular assessments identify vulnerabilities and weaknesses in the system.
- The benefits of proactive security measures: Proactive measures prevent potential breaches rather than reacting to them after the fact.
Regular audits and penetration testing are essential for maintaining a strong security posture and identifying areas for improvement.
Conclusion
The case of the cybercriminal netting millions through an Office365 executive account compromise serves as a stark reminder of the significant financial and reputational risks associated with inadequate cybersecurity measures. The attack highlighted the effectiveness of sophisticated phishing techniques, the vulnerability of weak passwords, and the critical need for multi-factor authentication. Implementing robust MFA, comprehensive security awareness training, advanced threat protection, and regular security audits are essential steps in preventing similar attacks. The long-term costs of a data breach far outweigh the investment in robust security measures.
Call to Action: Protect your business from the devastating consequences of an Office365 executive account compromise. Implement robust security measures today! Learn more about strengthening your Office365 security and preventing similar attacks. Don't wait until it's too late – secure your executive accounts now.

Featured Posts
-
 Google Search Ai Continued Training On Web Data Post Opt Out
May 04, 2025
Google Search Ai Continued Training On Web Data Post Opt Out
May 04, 2025 -
 Chinas Electric Motor Monopoly Alternatives And Solutions
May 04, 2025
Chinas Electric Motor Monopoly Alternatives And Solutions
May 04, 2025 -
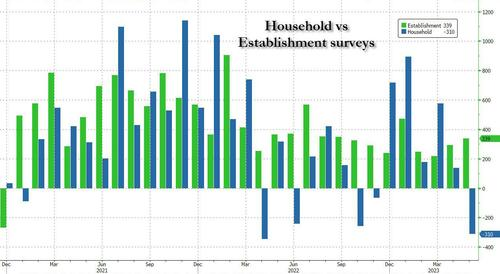 U S Economy Adds 177 000 Jobs In April Unemployment Rate Holds At 4 2
May 04, 2025
U S Economy Adds 177 000 Jobs In April Unemployment Rate Holds At 4 2
May 04, 2025 -
 How To Stream The Chicago Cubs Vs La Dodgers Mlb Game In Tokyo
May 04, 2025
How To Stream The Chicago Cubs Vs La Dodgers Mlb Game In Tokyo
May 04, 2025 -
 000d Kg Loai Qua Quy Hiem Duoc Dan Thanh Pho San Lung
May 04, 2025
000d Kg Loai Qua Quy Hiem Duoc Dan Thanh Pho San Lung
May 04, 2025
Latest Posts
-
 Obraz Emmi Stoun U Minispidnitsi Premiya Shou Biznesu
May 04, 2025
Obraz Emmi Stoun U Minispidnitsi Premiya Shou Biznesu
May 04, 2025 -
 Emma Stones Popcorn Dress A Snl 50th Anniversary Showstopper
May 04, 2025
Emma Stones Popcorn Dress A Snl 50th Anniversary Showstopper
May 04, 2025 -
 Oskar 2024 I Entasi Anamesa Stin Emma Stooyn Kai Tin Margkaret Koyalei
May 04, 2025
Oskar 2024 I Entasi Anamesa Stin Emma Stooyn Kai Tin Margkaret Koyalei
May 04, 2025 -
 Emma Stooyn Kai Margkaret Koyalei Tsakomos Sta Oskar Analysi Vinteo
May 04, 2025
Emma Stooyn Kai Margkaret Koyalei Tsakomos Sta Oskar Analysi Vinteo
May 04, 2025 -
 I Emma Stooyn Forese Ena Forema Poy Syzitietai Deite Pos
May 04, 2025
I Emma Stooyn Forese Ena Forema Poy Syzitietai Deite Pos
May 04, 2025
