Cybercriminal's Office365 Exploit: Millions In Losses For Executives
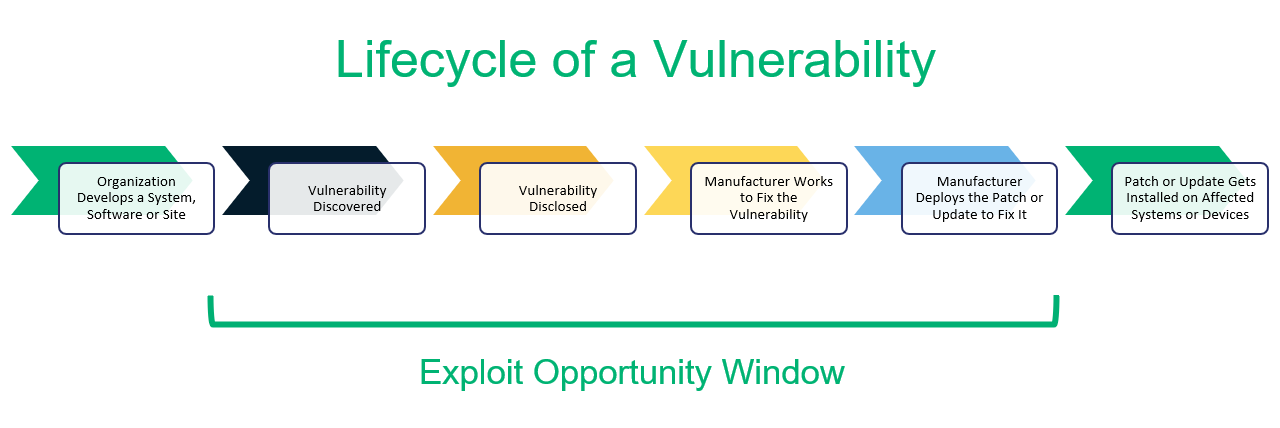
Table of Contents
How Cybercriminals Exploit Office365
Cybercriminals employ various methods to exploit the Office365 platform, often targeting executives due to their access to sensitive financial information and decision-making power. These exploits represent a significant threat to cybersecurity.
Phishing and Spoofing Attacks
Attackers frequently use phishing and spoofing to trick users into revealing credentials or initiating fraudulent transactions. This often involves CEO fraud, where the attacker impersonates a high-ranking executive to convince employees to transfer funds or disclose sensitive data.
- Spear Phishing and Whaling: These highly targeted attacks use personalized information to increase their effectiveness. Spear phishing targets specific individuals, while whaling focuses on high-profile executives (like CEOs or CFOs).
- Realistic Email Templates and URLs: Sophisticated attacks use nearly identical email templates and URLs to legitimate company communications, making them difficult to detect.
- Common Phishing Indicators:
- Unusual email addresses or domains.
- Urgent or threatening language.
- Grammatical errors and typos.
- Suspicious links or attachments.
- Requests for sensitive information.
Compromised Accounts and Malware
Gaining access to accounts is another common tactic. Attackers use several methods:
- Credential Stuffing: Using stolen credentials from other breaches to attempt logins.
- Brute-Force Attacks: Trying numerous password combinations until a successful login is achieved.
- Exploiting Third-Party App Vulnerabilities: Targeting vulnerabilities in applications integrated with Office365.
- Malware: Installing malware to maintain persistent access and exfiltrate data. This can include keyloggers, which record keystrokes, and data-stealing Trojans.
Multi-factor authentication (MFA) is crucial to prevent account compromise. Steps to prevent account compromise include strong, unique passwords, regular password changes, and enabling MFA.
Exploiting Office365 API Vulnerabilities
While less common, exploiting vulnerabilities in the Office365 API itself can allow attackers to access sensitive data without directly compromising user accounts. This requires advanced technical skills.
- API vulnerabilities: Attackers can exploit poorly secured APIs or misconfigurations to gain unauthorized access to data.
- Software Updates and Security Patches: Regularly updating Office365 and related applications is essential to patching known vulnerabilities.
- API Security Best Practices: Implementing strong authentication, authorization, and input validation for all API endpoints is crucial.
The Devastating Consequences of an Office365 Exploit
The consequences of a successful Office365 exploit can be severe and far-reaching.
Financial Losses
Successful attacks lead to significant financial losses:
- Wire Fraud: Transferring funds to attacker-controlled accounts.
- Invoice Scams: Modifying invoices to redirect payments.
- Ransomware Demands: Encrypting data and demanding a ransom for its release.
- Average Cost of a Data Breach: The cost can run into millions, including investigation, remediation, and legal fees. Reputational damage further compounds these costs.
Reputational Damage and Legal Ramifications
Beyond financial losses, an Office365 exploit causes serious reputational damage:
- Loss of Customer Trust: Damage to brand reputation impacting customer loyalty and future business.
- Legal Liabilities: Potential lawsuits from affected customers and regulatory fines (GDPR, CCPA).
- Loss of Investor Confidence: Negative impact on stock prices and investment opportunities.
Data Breaches and Intellectual Property Theft
Data breaches are a major consequence of Office365 exploits:
- Sensitive Customer Data: Names, addresses, financial information, and other personally identifiable information (PII).
- Confidential Business Information: Strategic plans, financial reports, and intellectual property.
- Intellectual Property Theft: Loss of trade secrets, patents, and copyrights.
- Identity Theft: Victims may experience identity theft and other related crimes. Remediation and recovery costs can be substantial.
Protecting Your Organization from Office365 Exploits
Protecting your organization from Office365 exploits requires a multi-layered approach.
Implementing Strong Security Measures
Several steps can significantly improve security:
- Multi-Factor Authentication (MFA): Implement MFA for all Office365 accounts.
- Security Awareness Training: Regular training for employees to recognize phishing attempts and other social engineering tactics.
- Robust Email Filtering and Anti-Phishing Solutions: Employ advanced email security solutions.
- Data Loss Prevention (DLP) Tools: Monitor and prevent sensitive data from leaving the organization's control.
Regular Security Audits and Vulnerability Assessments
Proactive security monitoring is crucial:
- Penetration Testing: Simulate real-world attacks to identify vulnerabilities.
- Regular Software Updates and Patching: Stay up-to-date with security patches for Office365 and all related software.
- Threat Intelligence Feeds: Stay informed about emerging threats and vulnerabilities.
Incident Response Planning
A well-defined plan is essential:
- Incident Response Plan: A documented plan outlining steps to take in the event of a security incident.
- Collaboration with Cybersecurity Experts: Seek professional help if an exploit occurs.
Conclusion:
The threat of an Office365 exploit is a serious concern for businesses of all sizes. Cybercriminals constantly develop new techniques, resulting in substantial financial losses, reputational damage, and legal repercussions. By implementing robust security measures, conducting regular security audits, and developing a comprehensive incident response plan, businesses can significantly reduce vulnerability. Don't wait until it's too late; proactively address the risk of an Office365 exploit and protect your organization today. Learn more about securing your Office365 environment and preventing costly executive email compromise by exploring resources on [link to relevant resource].

Featured Posts
-
 A Sneak Peek Anthony Mackie Stars In New Family Film
May 12, 2025
A Sneak Peek Anthony Mackie Stars In New Family Film
May 12, 2025 -
 Victoria De Knicks Sobre 76ers Anunoby Con Destacada Actuacion De 27 Puntos
May 12, 2025
Victoria De Knicks Sobre 76ers Anunoby Con Destacada Actuacion De 27 Puntos
May 12, 2025 -
 Boris Dzhonson Oproverg Slova Trampa O Reytinge Zelenskogo
May 12, 2025
Boris Dzhonson Oproverg Slova Trampa O Reytinge Zelenskogo
May 12, 2025 -
 Revelation Mask Singer 2025 L Identite De L Autruche Choque Laurent Ruquier
May 12, 2025
Revelation Mask Singer 2025 L Identite De L Autruche Choque Laurent Ruquier
May 12, 2025 -
 Prince Andrew Accusers Claim Facing Death After Bus Accident
May 12, 2025
Prince Andrew Accusers Claim Facing Death After Bus Accident
May 12, 2025
Latest Posts
-
 Vatican Succession Weighing The Options For Pope Francis Replacement
May 12, 2025
Vatican Succession Weighing The Options For Pope Francis Replacement
May 12, 2025 -
 Next Papal Election Examining The Leading Candidates And Their Platforms
May 12, 2025
Next Papal Election Examining The Leading Candidates And Their Platforms
May 12, 2025 -
 Nine Potential Popes Analyzing The Leading Candidates
May 12, 2025
Nine Potential Popes Analyzing The Leading Candidates
May 12, 2025 -
 The Next Pope Exploring The Profiles Of Potential Candidates For The Papacy
May 12, 2025
The Next Pope Exploring The Profiles Of Potential Candidates For The Papacy
May 12, 2025 -
 Pope Francis Successor A Conclave Of Nine
May 12, 2025
Pope Francis Successor A Conclave Of Nine
May 12, 2025
