Cybercriminal's Office365 Heist: Millions In Losses From Executive Email Compromise
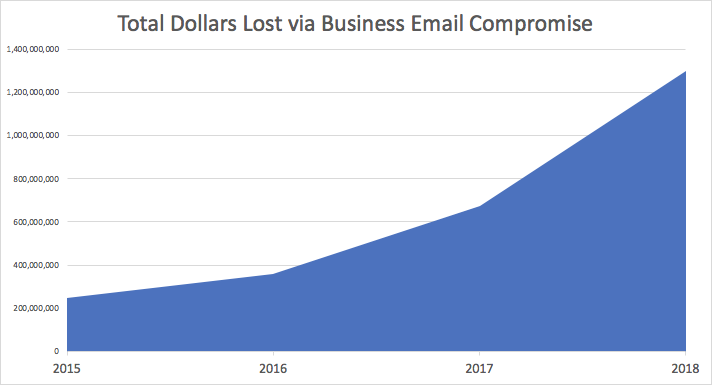
Table of Contents
How Cybercriminals Exploit Office365 for Executive Email Compromise
Cybercriminals leverage several attack vectors to exploit Office365 for executive email compromise. These include: phishing, spear phishing, credential stuffing, and business email compromise (BEC). They employ sophisticated techniques to bypass multi-factor authentication (MFA) and other security measures.
- Phishing Attacks: These attacks use deceptive emails to trick users into revealing sensitive information, such as usernames, passwords, and financial data. Often, these emails appear to come from legitimate sources, such as banks or online retailers.
- Spear Phishing: A more targeted form of phishing, spear phishing involves sending emails specifically designed to target a particular individual or organization. Cybercriminals often gather information about their target beforehand to increase the likelihood of success.
- Credential Stuffing: This involves using stolen usernames and passwords from other data breaches to attempt to access Office365 accounts. Often, these stolen credentials are obtained from dark web marketplaces.
- Business Email Compromise (BEC): BEC attacks typically involve the compromise of an executive's email account, followed by the sending of fraudulent emails to employees, vendors, or clients requesting wire transfers or other sensitive information.
Bypassing Security: Cybercriminals employ various methods to bypass MFA. These can include:
- Exploiting Weak Passwords: Guessing weak passwords or using password-cracking tools.
- Social Engineering: Manipulating employees into revealing MFA codes or bypassing security measures.
- Compromising Third-Party Apps: Exploiting vulnerabilities in third-party applications integrated with Office365.
Real-World Examples:
- Spoofed email addresses mimicking executives or trusted vendors requesting urgent wire transfers.
- Emails containing malicious links or attachments that install malware on the victim's computer.
- Compromised accounts used to send fraudulent invoices or purchase orders.
Keywords: Phishing attacks, Spear phishing, BEC scams, MFA bypass, Office365 vulnerabilities
The Devastating Financial Impact of Office365 Executive Email Compromise
Successful EEC attacks lead to significant financial losses, impacting organizations severely. The average financial loss can range from hundreds of thousands to millions of dollars, depending on the scale and scope of the attack.
- Financial Losses: Millions of dollars lost in fraudulent wire transfers, invoice payments, and other financial transactions.
- Reputational Damage: Data breaches erode trust, harming brand reputation and customer loyalty.
- Legal and Regulatory Consequences: Companies face hefty fines for non-compliance with regulations like GDPR, as well as legal costs associated with lawsuits and investigations.
- Loss of Intellectual Property: Sensitive data and intellectual property stolen during the attack can cause long-term damage to the business.
Case Studies: Numerous organizations have faced massive financial losses due to Office365 EEC attacks. For example, one case involved an organization losing $20 million due to a fraudulent wire transfer initiated through a compromised executive email account.
Keywords: Financial losses, Reputational damage, Data breach costs, GDPR compliance, Legal liabilities
Protecting Your Organization from Office365 Executive Email Compromise
Robust email security is crucial to protect against Office365 executive email compromise. Implementing strong security measures is essential for mitigating the risk.
- Multi-Factor Authentication (MFA): Enforce strong MFA across all accounts. This significantly increases the difficulty for attackers to gain unauthorized access.
- Advanced Threat Protection: Utilize Office365's advanced threat protection features to detect and block malicious emails and attachments.
- Security Awareness Training: Regularly train employees to identify and avoid phishing scams and other social engineering attacks.
- Email Authentication Protocols (SPF, DKIM, DMARC): Implement these protocols to authenticate emails and prevent spoofing attacks.
- Strong Password Policies & Access Control: Enforce strong password policies, regular password changes, and robust access control measures to limit access to sensitive information.
- Regular Security Audits: Conduct regular security assessments to identify and address potential vulnerabilities.
- Email Security Solutions: Consider employing third-party email security solutions with advanced threat detection capabilities.
Keywords: Email security solutions, Multi-factor authentication (MFA), Threat protection, Security awareness training, Access control, Cybersecurity best practices
Conclusion: Safeguarding Your Business from Office365 Executive Email Compromise
Executive email compromise targeting Office365 poses a significant threat to businesses of all sizes. The financial and reputational consequences of a successful attack can be devastating. By proactively implementing robust security measures, including MFA, advanced threat protection, and regular security awareness training, organizations can significantly reduce their risk. Don't become the next victim of an Office365 executive email compromise. Take action today by implementing robust security measures and safeguarding your business from this devastating cyber threat. Invest in comprehensive Office365 security and prioritize executive email compromise prevention to protect your valuable data and reputation. Explore cybersecurity solutions tailored for data protection and secure your future.

Featured Posts
-
 Yankees Vs Rays Series Injury Report May 2 4
May 12, 2025
Yankees Vs Rays Series Injury Report May 2 4
May 12, 2025 -
 Bayern Munich L Intelligence Tactique De Thomas Mueller Revelee Par Un Echange Avec Un Journaliste
May 12, 2025
Bayern Munich L Intelligence Tactique De Thomas Mueller Revelee Par Un Echange Avec Un Journaliste
May 12, 2025 -
 The Witcher Season 4 Liam Hemsworth Replaces Henry Cavill What Happened
May 12, 2025
The Witcher Season 4 Liam Hemsworth Replaces Henry Cavill What Happened
May 12, 2025 -
 Ufc 315 Full Fight Card Breakdown And Predictions
May 12, 2025
Ufc 315 Full Fight Card Breakdown And Predictions
May 12, 2025 -
 Sylvester Stallones Involvement In Jason Stathams Latest Film Expectations Vs Reality
May 12, 2025
Sylvester Stallones Involvement In Jason Stathams Latest Film Expectations Vs Reality
May 12, 2025
Latest Posts
-
 Edan Alexander Updates On The Kidnapping In Gaza
May 13, 2025
Edan Alexander Updates On The Kidnapping In Gaza
May 13, 2025 -
 Gaza Hostage Situation A Continuing Nightmare For Families
May 13, 2025
Gaza Hostage Situation A Continuing Nightmare For Families
May 13, 2025 -
 Gaza Kidnapping The Ongoing Search For Edan Alexander
May 13, 2025
Gaza Kidnapping The Ongoing Search For Edan Alexander
May 13, 2025 -
 The Unending Ordeal Gaza Hostages And Their Families
May 13, 2025
The Unending Ordeal Gaza Hostages And Their Families
May 13, 2025 -
 The Nightmare Of Gaza The Plight Of Hostage Families
May 13, 2025
The Nightmare Of Gaza The Plight Of Hostage Families
May 13, 2025
