Cybercriminal's Office365 Heist: Millions In Losses Reported

Table of Contents
The Methods Behind Office365 Attacks
Cybercriminals employ various sophisticated techniques to penetrate Office365 security. Understanding these methods is the first step towards effective protection.
Phishing and Spear Phishing
Phishing attacks exploit human error, relying on deceptive emails or messages to trick users into revealing their credentials. Spear phishing is a more targeted approach, personalizing the attack to increase its success rate.
- Examples of phishing emails: Emails appearing to be from legitimate sources like banks, payment processors, or even internal IT departments, requesting password changes or containing malicious links.
- Techniques to appear legitimate: Sophisticated email spoofing, use of company logos and branding, urgent or threatening language to pressure users into immediate action.
- Social engineering: Manipulating users' psychology to gain their trust and encourage them to divulge sensitive information.
- Statistics: Phishing remains incredibly effective, with studies showing success rates exceeding 20% in some cases.
Credential Stuffing and Brute-Force Attacks
These automated attacks leverage stolen credentials obtained from other data breaches or systematically try numerous password combinations to gain access.
- Effectiveness of multi-factor authentication (MFA): MFA significantly reduces the effectiveness of credential stuffing and brute-force attacks by requiring more than just a password for account access.
- Importance of strong password policies: Enforcing strong, unique passwords and regular password changes minimizes the vulnerability to brute-force attacks.
Exploiting Vulnerabilities
Attackers actively search for and exploit security flaws within Office365 itself or its related applications.
- Importance of keeping software updated: Regularly updating Office365 and related applications patches known security vulnerabilities, minimizing the risk of exploitation.
- Role of zero-day exploits: These are vulnerabilities that are unknown to the software vendor, making them particularly dangerous.
Malware and Ransomware
Malicious software is frequently used to gain unauthorized access and control over accounts and systems.
- Types of malware used: Keyloggers, spyware, Trojans, and ransomware are all commonly used to compromise Office365 accounts.
- Data exfiltration techniques: Attackers employ various methods to steal data, including direct access, cloud storage exploitation, and compromised email accounts.
- Ransomware demands and payment methods: Ransomware encrypts data and demands payment for its release. Payments are often requested through cryptocurrency transactions.
The Impact of Office365 Security Breaches
The consequences of an Office365 security breach extend far beyond the initial compromise, causing significant damage across multiple areas.
Financial Losses
The financial impact of an Office365 breach can be crippling.
- Lost revenue: Disruption of business operations, loss of customer trust, and decreased productivity lead to substantial revenue losses.
- Legal fees: Investigating and responding to a breach requires significant legal expertise and associated costs.
- Recovery costs: Restoring data, repairing systems, and implementing new security measures involve substantial financial investments.
- Examples of real-world cases: Numerous high-profile breaches have resulted in millions of dollars in losses for affected organizations.
Reputational Damage
A security breach severely damages a company's reputation and brand trust.
- Loss of customer confidence: Customers are hesitant to do business with organizations that have experienced data breaches.
- Damage to investor relations: Breaches negatively impact investor confidence and can lead to decreased stock prices.
Legal and Regulatory Compliance Issues
Organizations face significant legal and regulatory repercussions following a breach.
- GDPR, CCPA, and other relevant regulations: Failure to comply with data protection regulations results in hefty fines and legal action.
- Potential for lawsuits: Affected individuals and businesses can file lawsuits seeking compensation for damages.
Data Loss and Intellectual Property Theft
Sensitive data and intellectual property are often the primary targets in Office365 breaches.
- Consequences of data breaches: Identity theft, financial fraud, and reputational damage affect both individuals and organizations.
- Competitive disadvantage: Loss of intellectual property can put a company at a significant competitive disadvantage.
Protecting Your Organization from Office365 Attacks
Proactive security measures are crucial to preventing Office365 security breaches.
Implementing Strong Security Measures
A multi-layered security approach is necessary for effective protection.
- Multi-factor authentication (MFA): MFA adds an extra layer of security, requiring multiple forms of authentication to access accounts.
- Strong password policies: Enforce strong, unique passwords and regular password changes.
- Regular security audits: Conduct regular security assessments to identify vulnerabilities and weaknesses.
- Employee security training: Educate employees about phishing scams, social engineering tactics, and best security practices.
- Data loss prevention (DLP) tools: DLP solutions monitor and prevent sensitive data from leaving the organization's control.
- Endpoint detection and response (EDR) solutions: EDR provides advanced threat detection and response capabilities.
- Regular software updates: Keep Office365 and all related applications up-to-date with the latest security patches.
Utilizing Advanced Threat Protection (ATP)
Microsoft's Advanced Threat Protection (ATP) offers robust protection against sophisticated threats.
- Features offered by ATP: Real-time threat detection, malware protection, anti-phishing capabilities, and secure email gateways.
- How it detects and mitigates threats: ATP uses machine learning and advanced algorithms to identify and neutralize malicious activity.
Developing an Incident Response Plan
A well-defined incident response plan is vital for effectively handling a security breach.
- Key steps in an incident response plan: Detection, containment, eradication, recovery, and post-incident activity.
- Role of IT security professionals: Experienced IT security professionals are crucial for implementing and executing an effective incident response plan.
Conclusion
Office365 security breaches pose a significant threat to businesses of all sizes, resulting in substantial financial losses, reputational damage, and legal consequences. The methods used by cybercriminals are constantly evolving, necessitating a proactive and multi-layered security approach. Implementing strong security measures, leveraging advanced threat protection tools like Microsoft ATP, and developing a robust incident response plan are crucial steps in protecting your organization from becoming the next victim of an Office365 security breach. Don't wait until it's too late – take action today to safeguard your valuable data and protect your business. Consider investing in professional security assessments and consulting services to further enhance your Office365 security posture.

Featured Posts
-
 Frances Impressive Six Nations Performance Irelands Challenge
May 01, 2025
Frances Impressive Six Nations Performance Irelands Challenge
May 01, 2025 -
 Wayne Gretzkys Nhl Goal Record Tied By Alex Ovechkin Cp News Alert
May 01, 2025
Wayne Gretzkys Nhl Goal Record Tied By Alex Ovechkin Cp News Alert
May 01, 2025 -
 Englands Last Minute Victory A Thrilling Match Against France
May 01, 2025
Englands Last Minute Victory A Thrilling Match Against France
May 01, 2025 -
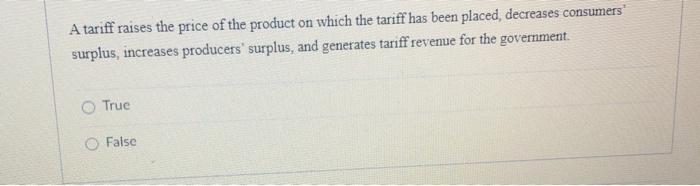 Retailers Brace For Tariff Price Increases
May 01, 2025
Retailers Brace For Tariff Price Increases
May 01, 2025 -
 Investigation Into Multi Million Dollar Nfl Player Robberies Chilean Migrants Arrested
May 01, 2025
Investigation Into Multi Million Dollar Nfl Player Robberies Chilean Migrants Arrested
May 01, 2025
Latest Posts
-
 Caso Becciu Oltre Il Danno La Beffa Del Risarcimento Agli Accusatori
May 01, 2025
Caso Becciu Oltre Il Danno La Beffa Del Risarcimento Agli Accusatori
May 01, 2025 -
 Papa Card Becciu Preghiere Ed Effetti Riflessioni Sulle Dimissioni
May 01, 2025
Papa Card Becciu Preghiere Ed Effetti Riflessioni Sulle Dimissioni
May 01, 2025 -
 Cardinale Becciu Appello In Partenza Il 22 Settembre Ribadisce La Sua Innocenza
May 01, 2025
Cardinale Becciu Appello In Partenza Il 22 Settembre Ribadisce La Sua Innocenza
May 01, 2025 -
 Usps Mail Delays Louisville Congressman Demands Greater Transparency
May 01, 2025
Usps Mail Delays Louisville Congressman Demands Greater Transparency
May 01, 2025 -
 Il Risarcimento Di Becciu Una Beffa Oltre Il Danno Subito Dagli Accusatori
May 01, 2025
Il Risarcimento Di Becciu Una Beffa Oltre Il Danno Subito Dagli Accusatori
May 01, 2025
