Federal Investigation: Millions Stolen Via Office365 Breaches

Table of Contents
Common Tactics Used in Office365 Breaches Leading to Millions Stolen
Cybercriminals employ increasingly sophisticated tactics to exploit vulnerabilities in Office365, leading to significant financial losses. These breaches are not isolated incidents; they represent a growing threat to businesses of all sizes.
Phishing and Social Engineering
Sophisticated phishing emails and social engineering techniques are primary weapons in the arsenal of cybercriminals targeting Office365 users.
- Example 1: Emails mimicking legitimate notifications from Office365, prompting users to update their passwords or access compromised accounts.
- Example 2: Phishing campaigns utilizing personalized information obtained through data breaches to increase the likelihood of success.
- Example 3: Social engineering tactics involving phone calls or text messages designed to trick users into revealing sensitive information, including login credentials.
Attackers cleverly leverage these tactics to gain access to credentials and subsequently infiltrate Office365 accounts, leading to data breaches and financial theft.
Exploiting Weak Passwords and Security Gaps
Many Office365 breaches stem from weak or easily guessed passwords. Cybercriminals utilize brute-force attacks (trying numerous password combinations) and password spraying (trying the same password across multiple accounts) to gain unauthorized access.
- Importance of Strong Passwords: Use strong, unique passwords for each account, combining uppercase and lowercase letters, numbers, and symbols.
- Multi-Factor Authentication (MFA): MFA is crucial. It adds an extra layer of security by requiring a second form of verification, such as a code from a mobile app or a security key, even if your password is compromised.
Malware and Ransomware Attacks
Malicious software, including ransomware, plays a significant role in Office365 breaches. These attacks often involve:
- Data Exfiltration: Attackers gain access to sensitive data, including financial records and customer information, and exfiltrate it to external servers.
- Ransom Demands: Ransomware encrypts data, making it inaccessible unless a ransom is paid. This can lead to significant financial losses and disruption of business operations.
- Advanced Persistent Threats (APTs): In some cases, sophisticated attackers utilize advanced persistent threats, remaining undetected within the system for extended periods to steal data gradually.
The Devastating Financial Impact of Office365 Data Breaches
The financial ramifications of Office365 data breaches are severe, extending far beyond the immediate monetary losses.
Direct Financial Losses
Millions of dollars are stolen directly through compromised accounts, impacting businesses' bottom lines. Beyond the direct theft, there are significant additional costs:
- Lost Revenue: Business interruptions and loss of productivity due to system downtime.
- Legal Fees: Costs associated with legal proceedings, regulatory investigations, and potential lawsuits.
- Recovery Costs: Expenses incurred in restoring data, enhancing security, and notifying affected parties. Examples include high-profile companies like [mention a real-world example of a company impacted by Office365 breach and its financial impact].
Reputational Damage and Loss of Customer Trust
The long-term consequences of Office365 breaches can be devastating. The damage to reputation and loss of customer trust are substantial, often leading to:
- Negative Publicity: Breaches can result in negative media coverage, impacting brand image and customer loyalty.
- Loss of Business: Customers may switch to competitors due to concerns about data security and privacy.
- Decreased Investor Confidence: Stock prices can plummet, impacting the company's market value. Transparency and a quick, effective response are crucial to mitigating reputational damage.
Strengthening Your Office365 Security to Prevent Millions from Being Stolen
Proactive security measures are paramount to preventing Office365 breaches.
Implementing Robust Multi-Factor Authentication (MFA)
MFA is no longer optional; it's a necessity. It significantly reduces the risk of unauthorized access, even if passwords are compromised. Methods include:
- Mobile App Authentication: Using authenticator apps like Microsoft Authenticator or Google Authenticator.
- Security Key Authentication: Employing physical security keys for an extra layer of protection.
- Email or SMS Verification: While less secure than other methods, it still provides additional security.
Regular Security Audits and Penetration Testing
Proactive security measures are crucial. Regular assessments identify and address vulnerabilities before they can be exploited:
- Vulnerability Assessments: Automated scans to identify potential security weaknesses.
- Penetration Testing: Simulated attacks to test the effectiveness of security controls.
Employee Security Awareness Training
Educating employees is critical. Regular training programs should cover:
- Phishing Recognition: Training employees to identify and report suspicious emails.
- Password Management: Enforcing strong password policies and promoting good password hygiene.
- Social Engineering Awareness: Educating employees on common social engineering tactics and how to avoid them.
Leveraging Advanced Security Features in Office365
Microsoft provides robust security features within Office365; utilize them:
- Microsoft Defender for Office 365: A cloud-based email security solution that protects against malware and phishing attacks.
- Conditional Access Policies: Allow you to define access rules based on user location, device, and other factors.
- Data Loss Prevention (DLP): Helps prevent sensitive data from leaving your organization's network. Refer to [link to Microsoft documentation] for detailed information.
Conclusion: Protecting Your Business from Office365 Breaches
Office365 breaches represent a significant threat, causing millions in financial losses and irreparable reputational damage. Proactive security measures are not just good practice; they are a business imperative. Implementing robust MFA, regular security audits, comprehensive employee training, and leveraging advanced Office365 security features are essential steps in protecting your organization. Don't let your business become the next victim of Office365 breaches. Take action today! Secure your organization against Office365 data breaches and protect millions.

Featured Posts
-
 Princess Dianas Bold Met Gala Choice The Untold Story Of An Altered Dress
May 06, 2025
Princess Dianas Bold Met Gala Choice The Untold Story Of An Altered Dress
May 06, 2025 -
 Warren Buffetts Greatest Investing Wins And Losses Key Lessons Learned
May 06, 2025
Warren Buffetts Greatest Investing Wins And Losses Key Lessons Learned
May 06, 2025 -
 I Dont Know Why Ariana Grande And Jeff Goldblums New Song
May 06, 2025
I Dont Know Why Ariana Grande And Jeff Goldblums New Song
May 06, 2025 -
 Ddg And Halle Bailey The Dont Take My Son Diss Track Explained
May 06, 2025
Ddg And Halle Bailey The Dont Take My Son Diss Track Explained
May 06, 2025 -
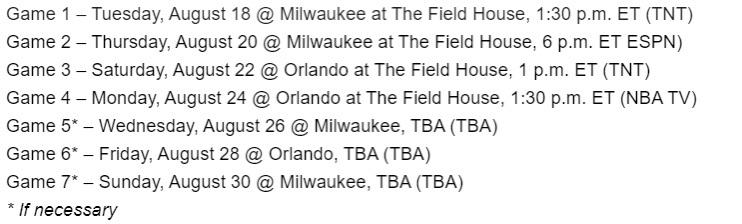 Celtics Vs Magic Playoff Schedule Full Dates And Times
May 06, 2025
Celtics Vs Magic Playoff Schedule Full Dates And Times
May 06, 2025
Latest Posts
-
 Nikes New Jordan Chiles And Sha Carri Richardson So Win Shirts A Closer Look
May 06, 2025
Nikes New Jordan Chiles And Sha Carri Richardson So Win Shirts A Closer Look
May 06, 2025 -
 Watch Beauty Schools Masterclass On Extra Long Nails
May 06, 2025
Watch Beauty Schools Masterclass On Extra Long Nails
May 06, 2025 -
 Met Gala 2025 Celebrity Guest List Speculation And Analysis
May 06, 2025
Met Gala 2025 Celebrity Guest List Speculation And Analysis
May 06, 2025 -
 Maintaining Extra Long Nails Advice From Beauty School
May 06, 2025
Maintaining Extra Long Nails Advice From Beauty School
May 06, 2025 -
 Predicting The Met Gala 2025 Guest List Celebrities We Expect To See
May 06, 2025
Predicting The Met Gala 2025 Guest List Celebrities We Expect To See
May 06, 2025
