Federal Investigation: Office365 Breach Nets Millions For Hacker

Table of Contents
The Scale of the Office365 Breach and its Impact
The Office365 breach affected an estimated 500 organizations, compromising sensitive data from thousands of accounts. The stolen data included a mix of highly sensitive information: financial records, intellectual property, confidential client information, and personal data like social security numbers and addresses. The financial losses suffered by victims are currently estimated to be in the tens of millions of dollars, a staggering figure that underscores the severity of the attack.
- Specific examples of compromised data: Payroll information, customer lists with personally identifiable information (PII), strategic business plans, and financial transaction records.
- Impact on businesses: The breach led to significant reputational damage, hefty legal fees related to compliance violations and potential lawsuits, and considerable operational disruption as businesses struggled to recover and secure their systems.
- Impact on individuals: Individuals whose personal information was compromised face the risks of identity theft, financial fraud, and ongoing monitoring of their credit reports.
Methods Used by the Hacker in the Office365 Breach
The hacker employed a multi-stage attack leveraging sophisticated techniques to gain access and exfiltrate data. Initial access was reportedly gained through a highly targeted phishing campaign, cleverly disguised as legitimate emails from trusted sources. Once inside the network, the hacker used malware to move laterally, gaining access to privileged accounts and exploiting vulnerabilities in older Office365 applications. The data exfiltration process involved using encrypted channels to avoid detection.
- Specific examples of hacking techniques: Spear phishing, credential stuffing, exploiting known vulnerabilities in older Office365 versions, and using custom malware to bypass security controls.
- Details about the malware used: While the specifics of the malware remain under investigation, reports suggest custom-built tools designed to avoid antivirus detection and blend seamlessly with legitimate system processes.
- Description of the data exfiltration process: Data was exfiltrated using encrypted tunnels and distributed across multiple servers, making it challenging for investigators to trace and recover.
The Federal Investigation into the Office365 Breach
The Federal Bureau of Investigation (FBI) is leading the federal investigation into this significant Office365 breach, collaborating with other agencies including the Cybersecurity and Infrastructure Security Agency (CISA). The investigation is ongoing, but initial findings suggest a highly organized and well-resourced criminal operation. While no arrests have been publicly announced yet, the investigation is actively pursuing leads and examining evidence to identify and prosecute the perpetrators. The hacker faces significant penalties, including lengthy prison sentences and substantial fines.
- Timeline of the investigation: The investigation began immediately after the breach was discovered and is expected to continue for several months.
- Key findings released by investigators: Limited information has been publicly released to avoid compromising the ongoing investigation.
- Potential legal ramifications for the hacker: The hacker could face charges under several federal laws, including the Computer Fraud and Abuse Act (CFAA) and various statutes related to identity theft and financial fraud.
Preventing Future Office365 Breaches: Cybersecurity Best Practices
Preventing future Office365 breaches requires a multi-layered approach to cybersecurity. Proactive measures are far more effective than reactive ones. Businesses must prioritize robust security practices to protect their sensitive data.
- Implement multi-factor authentication (MFA): MFA adds an extra layer of security, requiring users to provide multiple forms of authentication before gaining access.
- Enforce strong password policies: Require complex passwords and regularly change them. Consider using password managers to help users generate and manage secure passwords.
- Provide comprehensive employee training: Educate employees on phishing and social engineering tactics to minimize the risk of successful phishing attacks.
- Conduct regular security audits: Regularly assess your security posture to identify and address vulnerabilities before they can be exploited. Consider penetration testing to simulate real-world attacks.
- Keep software updated: Ensure all software, including Office365 applications, is updated with the latest security patches.
- Invest in robust security information and event management (SIEM) systems: SIEMs help monitor network activity and detect suspicious behavior.
Don't wait for a breach to happen. Take proactive steps to implement these security measures and build a strong cybersecurity foundation. Consider consulting with cybersecurity professionals for assistance in implementing and managing these solutions.
Conclusion: Protecting Your Business from Office365 Breaches
This Office365 breach underscores the devastating financial and reputational damage that can result from a successful cyberattack. The scale of the breach, the sophistication of the hacker's methods, and the ongoing federal investigation highlight the critical need for proactive cybersecurity measures. Implementing robust Office365 security, including multi-factor authentication, strong password policies, employee training, and regular security audits, is paramount to protecting your business from similar attacks. Don't become the next victim of an Office365 breach. Implement strong cybersecurity practices and invest in comprehensive Office365 security solutions today!

Featured Posts
-
 Finding Funding For Sustainable Development In Your Sme
May 19, 2025
Finding Funding For Sustainable Development In Your Sme
May 19, 2025 -
 Performance Credit Mutuel Am Decryptage Des Resultats Du 4eme Trimestre 2024
May 19, 2025
Performance Credit Mutuel Am Decryptage Des Resultats Du 4eme Trimestre 2024
May 19, 2025 -
 Alfonso Arus Critica A Melody En Arusero Tras Su Eleccion Para Eurovision 2025
May 19, 2025
Alfonso Arus Critica A Melody En Arusero Tras Su Eleccion Para Eurovision 2025
May 19, 2025 -
 Traveling With Pets In Mumbai Your Uber Booking Guide
May 19, 2025
Traveling With Pets In Mumbai Your Uber Booking Guide
May 19, 2025 -
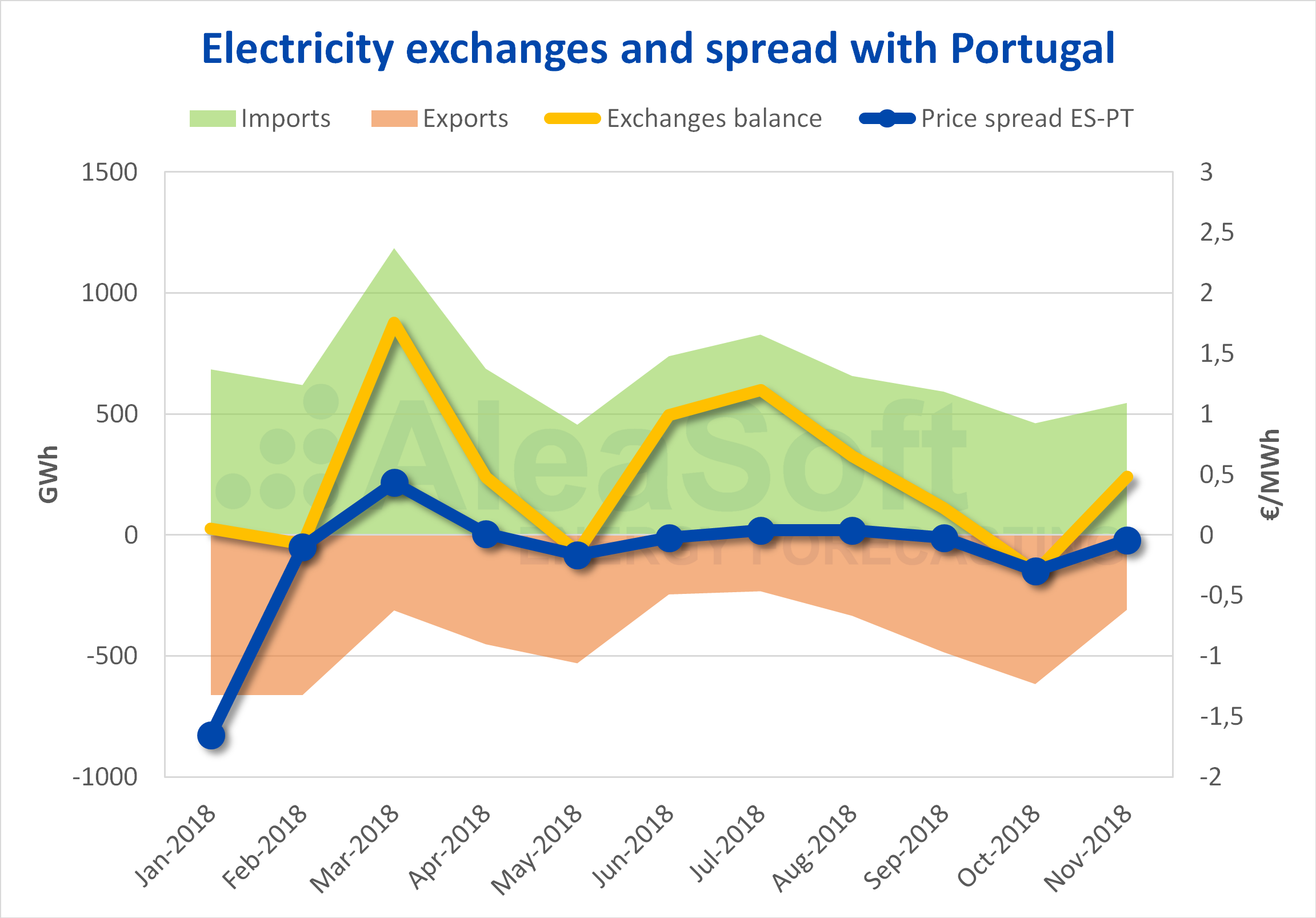 Blackout Prompts Portugal To Increase Electricity Imports From Spain
May 19, 2025
Blackout Prompts Portugal To Increase Electricity Imports From Spain
May 19, 2025
Latest Posts
-
 Analyzing The Latest Mlb Trade Rumors Luis Robert Jr Pirates And Arenado
May 19, 2025
Analyzing The Latest Mlb Trade Rumors Luis Robert Jr Pirates And Arenado
May 19, 2025 -
 Libraries In Crisis Staff And Service Reductions After Agency Closure
May 19, 2025
Libraries In Crisis Staff And Service Reductions After Agency Closure
May 19, 2025 -
 Mlb Rumors Roundup Luis Robert Jr Arenado And Key Trade Developments
May 19, 2025
Mlb Rumors Roundup Luis Robert Jr Arenado And Key Trade Developments
May 19, 2025 -
 The Crumbling Of Library Services Examining The Impact Of Agency Cuts
May 19, 2025
The Crumbling Of Library Services Examining The Impact Of Agency Cuts
May 19, 2025 -
 Distractions Loom As Clemson Kicks Off Spring Football Practice
May 19, 2025
Distractions Loom As Clemson Kicks Off Spring Football Practice
May 19, 2025
