Office365 Executive Inboxes Targeted: Crook Makes Millions, Authorities Say
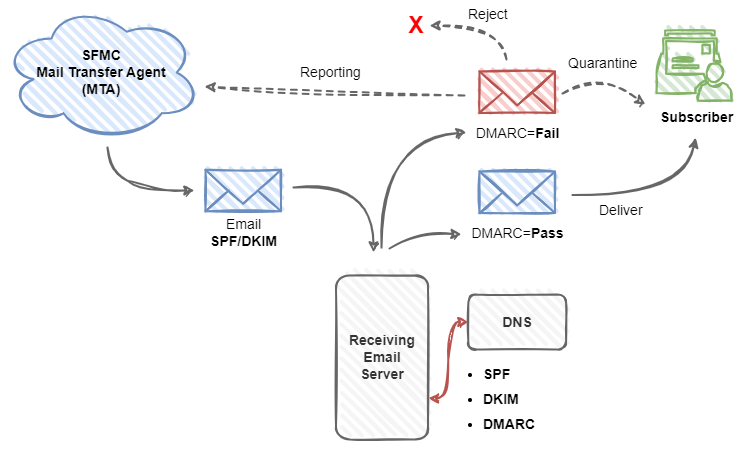
Table of Contents
Keywords: Office365, executive inbox, email security, phishing, cybercrime, data breach, Microsoft 365 security, CEO fraud, business email compromise (BEC), financial crime
A sophisticated cybercriminal has reportedly amassed millions of dollars by targeting the Office365 executive inboxes of numerous companies. This alarming case highlights the increasing vulnerability of high-level accounts to sophisticated phishing attacks and business email compromise (BEC) scams. This article delves into the details of this operation, examining the methods employed and offering crucial advice on bolstering your Office365 security to avoid becoming the next victim.
The Modus Operandi: How the Crook Targeted Office365 Executive Inboxes
The criminal employed a multi-pronged approach, leveraging various techniques to breach the robust security measures typically associated with executive-level Office365 accounts. This wasn't a simple phishing attempt; it was a carefully orchestrated campaign demonstrating advanced knowledge of both social engineering and technical vulnerabilities.
-
Highly personalized phishing emails mimicking legitimate communications: The attacker crafted emails that appeared to originate from trusted sources, such as board members, clients, or financial institutions. These emails often contained urgent requests for wire transfers or other sensitive actions. The level of personalization was key to their success, exploiting the trust placed in familiar communication styles and relationships.
-
Exploitation of known vulnerabilities in Office365: While Microsoft regularly releases patches and updates, even the most secure systems can be vulnerable if not properly maintained. The attacker likely exploited known vulnerabilities to gain initial access or escalate privileges within the Office365 environment. This underscores the importance of keeping software up-to-date and employing robust patch management strategies.
-
Use of compromised accounts to gain access: In some cases, the attacker may have compromised accounts of lower-level employees to gain access to the executive inboxes indirectly. This illustrates the principle that weak points in any part of the organization's security posture can be exploited to compromise even the most secure accounts.
-
Deployment of malware for data exfiltration: Once access was gained, malware may have been deployed to exfiltrate sensitive data, including financial records and communication logs. This data could then be used for further attacks or to facilitate fraudulent transactions.
The Financial Impact: Millions Lost Through Office365 Compromise
The financial impact of this cybercrime operation is staggering. Reports suggest millions of dollars were stolen from numerous organizations across various sectors. The consequences extended far beyond the immediate financial loss.
-
Significant financial losses for targeted companies: The direct loss of funds through wire fraud and fraudulent invoices is substantial, potentially crippling smaller businesses and severely impacting the bottom line of larger corporations.
-
Reputational damage and loss of investor confidence: A data breach, particularly one involving the compromise of executive accounts, can severely damage an organization's reputation and erode investor confidence, leading to further financial difficulties.
-
Legal and regulatory repercussions: Companies affected by such attacks often face legal and regulatory repercussions, including fines, lawsuits, and investigations by government agencies. Compliance with regulations like GDPR adds to the potential for significant penalties.
Authorities' Response and Ongoing Investigation: Tracking Down the Cybercriminal
Multiple law enforcement agencies, both domestically and internationally, are collaborating to track down the cybercriminal responsible for this widespread Office365 executive inbox compromise. This highlights the transnational nature of cybercrime and the need for international cooperation.
-
Collaboration between international law enforcement agencies: The scale and sophistication of the attack necessitate collaboration between agencies across borders to share intelligence and coordinate investigative efforts.
-
Ongoing investigations to identify other victims: Authorities are actively working to identify all victims of the attack and assess the full extent of the damage. This process is often complex and time-consuming.
-
Efforts to recover stolen funds: Recovering stolen funds is a significant challenge in cybercrime investigations. However, law enforcement agencies are pursuing all available avenues to recover the stolen assets.
Protecting Your Office365 Executive Inboxes: Best Practices and Security Measures
Protecting your organization from similar attacks requires a multi-layered approach encompassing technological solutions and employee awareness.
-
Implement multi-factor authentication (MFA) for all accounts: MFA adds an extra layer of security, significantly reducing the risk of unauthorized access even if credentials are compromised.
-
Regularly update Office365 software and security patches: Staying up-to-date with the latest patches and updates is critical for protecting against known vulnerabilities.
-
Conduct employee security awareness training: Educating employees about phishing techniques and social engineering tactics is crucial in preventing successful attacks. Regular training sessions should be implemented.
-
Utilize advanced threat protection features within Office365: Microsoft 365 offers advanced threat protection features, such as anti-phishing and anti-malware solutions, that should be fully utilized.
-
Implement email authentication protocols like DMARC, SPF, and DKIM: These protocols help verify the authenticity of emails, reducing the chances of receiving fraudulent communications.
-
Regularly review user access permissions: Regularly reviewing and limiting user access rights can minimize the potential damage from a compromised account.
-
Consider using email security solutions beyond native Office365 features: Additional email security solutions can provide an extra layer of protection against advanced threats.
Conclusion
The targeting of Office365 executive inboxes has resulted in significant financial losses and highlighted the critical need for robust email security measures. The sophistication of these attacks underscores the importance of a proactive approach to cybersecurity, including multi-factor authentication, regular software updates, and comprehensive employee training. Don't become another statistic – secure your Office365 executive inboxes today. Learn more about strengthening your Microsoft 365 security now and protect your organization from the devastating consequences of BEC and other sophisticated cyberattacks.

Featured Posts
-
 Abu Dhabi Open Belinda Bencic Back In The Final
Apr 27, 2025
Abu Dhabi Open Belinda Bencic Back In The Final
Apr 27, 2025 -
 Cerundolo En Cuartos De Indian Wells Tras Bajas De Fritz Y Gauff
Apr 27, 2025
Cerundolo En Cuartos De Indian Wells Tras Bajas De Fritz Y Gauff
Apr 27, 2025 -
 Pegula Defeats Collins In Thrilling Charleston Open Match
Apr 27, 2025
Pegula Defeats Collins In Thrilling Charleston Open Match
Apr 27, 2025 -
 German Politics Crumbachs Resignation Shakes Spd Bsw Coalition
Apr 27, 2025
German Politics Crumbachs Resignation Shakes Spd Bsw Coalition
Apr 27, 2025 -
 Ariana Grandes Hair And Tattoo Makeover The Importance Of Professional Assistance
Apr 27, 2025
Ariana Grandes Hair And Tattoo Makeover The Importance Of Professional Assistance
Apr 27, 2025
Latest Posts
-
 Understanding Ariana Grandes Style Choices Hair Tattoos And Professional Guidance
Apr 27, 2025
Understanding Ariana Grandes Style Choices Hair Tattoos And Professional Guidance
Apr 27, 2025 -
 Hair And Tattoo Transformations Learning From Ariana Grandes Style
Apr 27, 2025
Hair And Tattoo Transformations Learning From Ariana Grandes Style
Apr 27, 2025 -
 Ariana Grandes Bold New Look The Role Of Professional Expertise
Apr 27, 2025
Ariana Grandes Bold New Look The Role Of Professional Expertise
Apr 27, 2025 -
 Celebrity Style Transformation Ariana Grandes Hair And Tattoos
Apr 27, 2025
Celebrity Style Transformation Ariana Grandes Hair And Tattoos
Apr 27, 2025 -
 Professional Help For Hair And Tattoo Transformations Ariana Grandes Inspiration
Apr 27, 2025
Professional Help For Hair And Tattoo Transformations Ariana Grandes Inspiration
Apr 27, 2025
