Office365 Executive Inboxes Targeted: Millions Stolen In Cybercrime
Table of Contents
The Tactics Used in Targeting Executive Inboxes
Cybercriminals employ increasingly sophisticated techniques to target executive inboxes within the Office365 environment. These attacks leverage both social engineering and technical vulnerabilities to gain unauthorized access.
Highly Personalized Phishing Campaigns
These aren't your run-of-the-mill phishing emails. Attackers invest significant time and resources in creating highly personalized campaigns designed to bypass security filters and deceive even the most vigilant users.
- Focus on Detail: Phishing emails meticulously mimic known contacts, using genuine names, email addresses, and even incorporating company-specific information gleaned from publicly available sources like LinkedIn or company websites.
- Urgency and Authority: A sense of urgency and authority is often employed to pressure the recipient into immediate action. Emails might claim to be from a senior executive, a board member, or a trusted vendor demanding immediate payment or access to sensitive data.
- Examples: Common examples include fake invoice requests, urgent payment demands (often involving wire transfers), requests for sensitive information (like login credentials or financial details), or purportedly urgent requests for changes in company policy.
- Advanced Techniques: Spear phishing and whaling are common, highly targeted attacks designed to deceive specific individuals within an organization, typically those with significant financial authority or access to sensitive information. These attacks rely on detailed reconnaissance and the crafting of highly convincing emails.
Exploiting Vulnerabilities in Office365
Beyond social engineering, attackers exploit weaknesses within the Office365 platform itself. These vulnerabilities provide an entry point for malicious actors.
- Weak Passwords and Compromised Credentials: Weak or easily guessable passwords remain a primary target for attackers. Credential stuffing, using stolen credentials from other breaches, is a common tactic.
- Lack of Multi-Factor Authentication (MFA): The absence of MFA significantly weakens security. Even if a password is compromised, MFA adds an extra layer of protection, requiring a second form of verification, like a code from a mobile device or security key.
- Unpatched Software and Outdated Security Protocols: Failing to update Office365 software and neglecting to implement the latest security protocols leaves systems vulnerable to known exploits. Regular patching is essential.
- Compromised Third-Party Applications: Many businesses use third-party applications that integrate with Office365. If these applications are compromised, attackers may gain indirect access to sensitive data and email accounts.
The Devastating Consequences of a Successful Attack
A successful attack on Office365 executive inboxes can have far-reaching and devastating consequences, impacting not just finances but also the company's reputation and long-term viability.
Financial Losses
The financial impact can be catastrophic.
- Millions Stolen: Fraudulent wire transfers, initiated through compromised email accounts, are a primary method of theft, often resulting in the loss of millions of dollars.
- Investigation and Remediation Costs: Investigating a breach, remediating the compromised system, and restoring data can incur significant costs.
- Reputational Damage: The negative publicity associated with a data breach can severely damage a company's reputation, impacting investor confidence and customer loyalty, leading to decreased sales and lost business opportunities.
Data Breaches and Intellectual Property Theft
Beyond financial losses, successful attacks lead to the exposure of sensitive information.
- Exposure of Sensitive Customer Data: The theft of customer data exposes the company to regulatory fines and costly lawsuits, especially under regulations like GDPR or CCPA.
- Loss of Trade Secrets and Confidential Business Information: The theft of intellectual property can severely impact a company's competitive advantage and profitability.
- Disruption of Business Operations: A successful attack can severely disrupt business operations, leading to loss of productivity and significant downtime while systems are restored.
Protecting Your Office365 Executive Inboxes
Protecting against these targeted attacks requires a multi-layered approach combining technical security measures, employee training, and proactive monitoring.
Implementing Robust Security Measures
Implementing robust security measures is paramount to protecting your organization from sophisticated cyberattacks.
- Strong Password Policies and Multi-Factor Authentication (MFA): Enforce strong password policies and make MFA mandatory for all users, especially executives.
- Regular Security Awareness Training: Regular training for all employees, particularly executives, is crucial to educate them about phishing techniques and best practices for identifying and reporting suspicious emails.
- Advanced Threat Protection Tools and Email Security Solutions: Deploy advanced threat protection tools and email security solutions that can detect and block sophisticated phishing attempts and malware.
- Regular Software Updates and Patching: Regularly update and patch all Office365 software and applications to address known vulnerabilities.
Monitoring and Incident Response
Proactive monitoring and a well-defined incident response plan are essential.
- Real-Time Monitoring: Implement real-time monitoring of Office365 accounts for suspicious activity, such as unusual login attempts or large data transfers.
- Incident Response Protocols: Establish clear incident response protocols to minimize damage in case of a breach. This should include a plan for containing the breach, investigating its scope, and restoring affected systems.
- Cybersecurity Experts: Partnering with cybersecurity experts provides access to advanced threat detection and remediation capabilities.
Leveraging Microsoft 365 Security Features
Microsoft 365 offers a suite of security tools to enhance protection.
- Microsoft Defender for Office 365: Utilize Microsoft Defender for Office 365 for advanced threat protection, including anti-phishing and anti-malware capabilities.
- Data Loss Prevention (DLP) Policies: Configure DLP policies to safeguard sensitive information by preventing its unauthorized access, use, or transfer.
- Regular Security Settings Review: Regularly review and adjust security settings within the Office365 admin center to ensure optimal protection.
Conclusion
The targeting of Office365 executive inboxes is a serious and evolving threat, with potentially devastating financial and reputational consequences. By understanding the tactics used and implementing robust security measures, including multi-factor authentication, advanced threat protection, and regular security awareness training, businesses can significantly reduce their risk. Don't wait until it's too late. Secure your Office365 executive inboxes today and protect your business from the devastating impact of cybercrime. Learn more about strengthening your Office365 security and mitigating the risk of targeted attacks by researching available security solutions and best practices. Proactive investment in robust email security is crucial for preventing millions in losses from this growing threat.

Featured Posts
-
 Trgovine Otvorene Za Uskrs Pronadite Otvorene Ducane
Apr 23, 2025
Trgovine Otvorene Za Uskrs Pronadite Otvorene Ducane
Apr 23, 2025 -
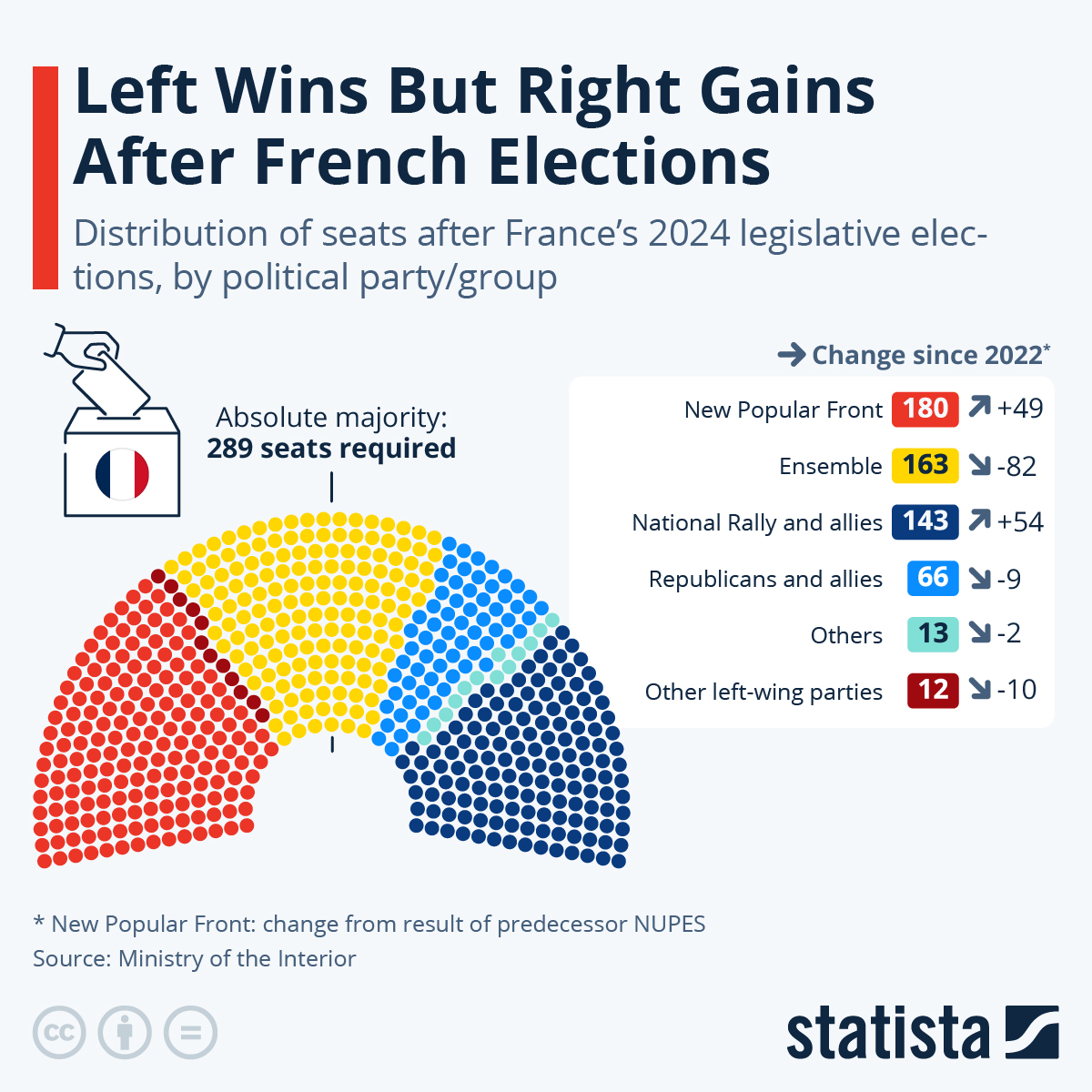 Early French Election Macrons Strategy And Potential Outcomes
Apr 23, 2025
Early French Election Macrons Strategy And Potential Outcomes
Apr 23, 2025 -
 Examining The Economic Data Wheres The Trump Effect
Apr 23, 2025
Examining The Economic Data Wheres The Trump Effect
Apr 23, 2025 -
 Auto Dealers Push Back Against Mandatory Ev Quotas
Apr 23, 2025
Auto Dealers Push Back Against Mandatory Ev Quotas
Apr 23, 2025 -
 Brewers Nine Base Steal Record Fuels Blowout Victory
Apr 23, 2025
Brewers Nine Base Steal Record Fuels Blowout Victory
Apr 23, 2025
