Crook's Office365 Exploit Results In Multi-Million Dollar Loss, FBI Investigation Underway

Table of Contents
Understanding the Office365 Exploit
An Office365 exploit refers to any malicious activity that leverages vulnerabilities within the Microsoft Office365 suite to gain unauthorized access to sensitive data or systems. These exploits can range from relatively simple phishing scams to complex, targeted attacks designed to bypass even the most sophisticated security measures. The potential for large-scale damage is immense, as Office365 is used by millions of businesses and individuals worldwide, holding a treasure trove of valuable information.
Common methods used in Office365 exploits include:
- Phishing: Malicious emails designed to trick users into revealing their login credentials or downloading malware. These often mimic legitimate communications from known organizations.
- Credential Stuffing: Using lists of stolen usernames and passwords to attempt logins to Office365 accounts. This often targets accounts with weak or reused passwords.
- Malware: Installing malicious software on a user's computer that can steal data, control the system, or provide access to the Office365 account.
- Exploiting Software Vulnerabilities: Taking advantage of unpatched security flaws in Office365 software or related applications.
Specific vulnerabilities often targeted include:
- Weak passwords: Easily guessable or reused passwords.
- Phishing emails with malicious links/attachments: Tricking users into clicking links or opening files that download malware or redirect to phishing websites.
- Compromised user accounts: Accounts accessed through stolen credentials or malware.
- Unpatched software vulnerabilities: Outdated software with known security flaws.
- Lack of multi-factor authentication: Failing to require multiple forms of authentication to access accounts.
Details of the Multi-Million Dollar Loss
While the precise amount of the financial loss remains undisclosed for competitive reasons, sources confirm the figure to be in the millions of dollars. The nature of the loss is believed to involve a combination of stolen funds and intellectual property theft, severely impacting the victim organization. The repercussions extend far beyond the immediate financial consequences.
The consequences faced by the victim include:
- Financial losses: Millions of dollars in lost funds and potential legal costs.
- Reputational damage: A significant blow to the company's public image and trust.
- Legal and regulatory ramifications: Potential fines and investigations from regulatory bodies.
- Operational disruption and downtime: Interruption of business operations, loss of productivity, and data recovery efforts.
The FBI Investigation and its Implications
The FBI's involvement highlights the seriousness of the crime and the potential for federal charges against the perpetrator(s). The investigation is likely focusing on several key areas, including tracing the source of the exploit, identifying the perpetrator, and recovering any stolen assets.
The FBI's investigative process likely includes:
- Tracing the source of the exploit: Identifying the origin point of the attack and the methods used.
- Identifying the perpetrator: Tracking down the individual or group responsible.
- Recovering stolen assets: Attempting to recover any stolen funds or intellectual property.
- Legal proceedings and potential sentencing: Preparing and presenting evidence for prosecution, leading to potential sentencing under relevant cybercrime laws.
The broader implications of this incident underscore the pervasive threat of Office365 exploits and the need for enhanced security protocols across all organizations.
Protecting Your Organization from Office365 Exploits
Preventing a similar Office365 exploit requires a multi-layered approach to cybersecurity. Implementing robust security measures is crucial for mitigating the risk. Proactive measures are far more effective than reactive damage control.
To protect your organization, consider these essential steps:
- Implement and enforce strong password policies: Require complex, unique passwords, and enforce regular password changes.
- Enable multi-factor authentication (MFA): Require multiple forms of authentication to access accounts, significantly reducing the risk of unauthorized access.
- Regularly update Office365 software and applications: Keep all software patched and updated to address known vulnerabilities.
- Conduct employee security awareness training: Educate employees about phishing scams, malware, and other common threats.
- Utilize advanced threat protection tools: Employ security solutions that monitor for suspicious activity and provide advanced threat protection.
- Monitor user activity for suspicious behavior: Regularly review user logins and activity for any unusual patterns.
Conclusion: Strengthening Your Office365 Security in the Face of Exploits
The multi-million dollar loss resulting from this Office365 exploit underscores the critical need for robust cybersecurity measures. The financial and reputational consequences of such attacks can be devastating. Don't underestimate the importance of proactive security measures. The FBI investigation highlights the serious nature of these crimes and the potential for severe legal repercussions. By implementing the security measures outlined above, you can significantly reduce your organization's vulnerability to Office365 exploits and protect your valuable data and reputation. Don't become the next victim – implement strong security measures for your Office365 environment today!

Featured Posts
-
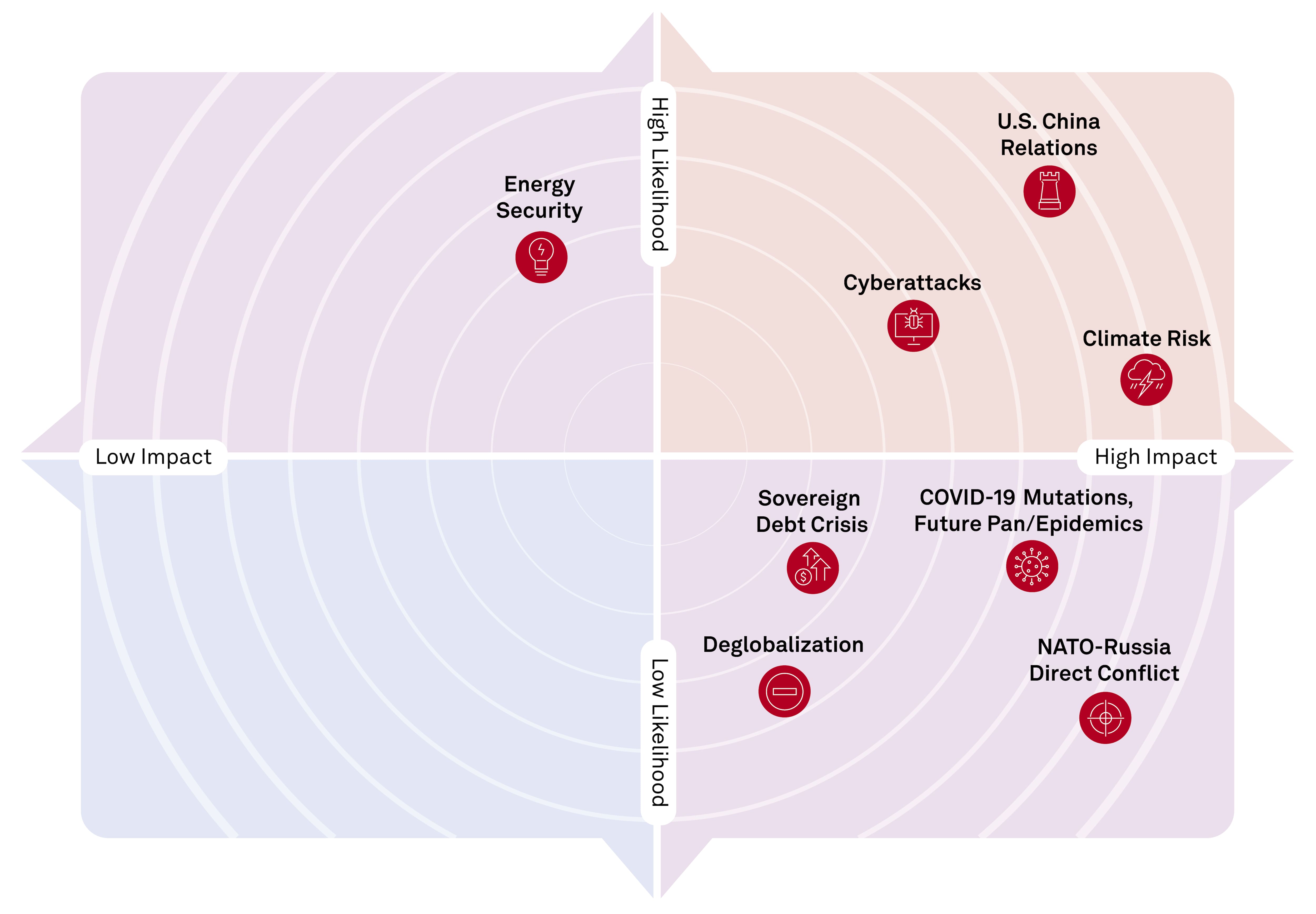 Greenlands Future Navigating The Geopolitical Shift After Trumps Actions
May 09, 2025
Greenlands Future Navigating The Geopolitical Shift After Trumps Actions
May 09, 2025 -
 Bundesliga Showdown Bayern Munich Vs Eintracht Frankfurt Match Analysis And Prediction
May 09, 2025
Bundesliga Showdown Bayern Munich Vs Eintracht Frankfurt Match Analysis And Prediction
May 09, 2025 -
 Elizabeth Hurley Shows Off Her Figure In Maldives Bikini Photos
May 09, 2025
Elizabeth Hurley Shows Off Her Figure In Maldives Bikini Photos
May 09, 2025 -
 Inter Milans Stunning Champions League Victory Over Bayern Munich
May 09, 2025
Inter Milans Stunning Champions League Victory Over Bayern Munich
May 09, 2025 -
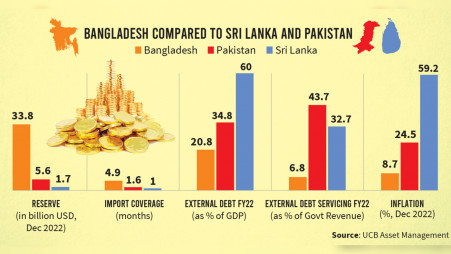 Pakistan Sri Lanka Bangladesh Pledge To Strengthen Capital Market Ties
May 09, 2025
Pakistan Sri Lanka Bangladesh Pledge To Strengthen Capital Market Ties
May 09, 2025
