Cybercriminal's Office365 Scheme: Millions In Losses Reported By Federal Authorities
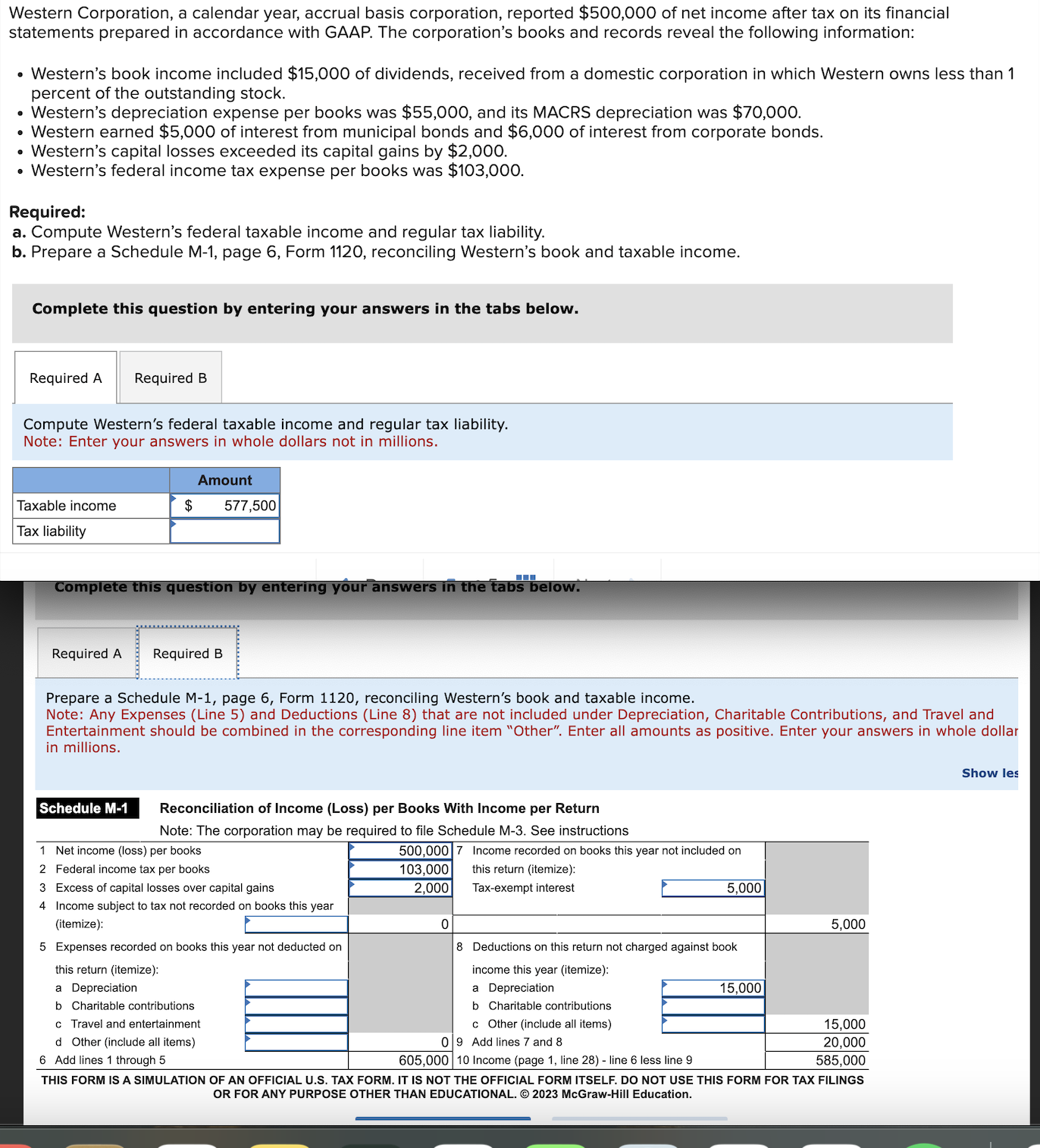
Table of Contents
Federal authorities have reported a significant surge in financial losses stemming from sophisticated cybercriminal schemes targeting Office365 accounts. Millions of dollars have been stolen through a variety of methods, highlighting the critical vulnerability of relying solely on default security settings within the popular Microsoft platform. This article details the tactics employed by cybercriminals, the devastating consequences, and crucial steps organizations can take to protect themselves from these devastating Office365 email compromise attacks. Understanding the threat landscape of Office 365 security is crucial for businesses of all sizes.
Common Tactics Used in Office365 Email Compromise Schemes
Cybercriminals employ a range of tactics to compromise Office365 accounts, leading to significant Office365 email compromise incidents. These attacks often exploit human error or vulnerabilities within the system.
Phishing and Spear Phishing Attacks
Attackers use deceptive emails to trick users into revealing their credentials or clicking malicious links. These emails often mimic legitimate communications, creating a sense of urgency or trust.
- Fake Login Pages: Phishing emails may contain links to fake login pages that closely resemble the legitimate Office365 login portal. Entering credentials on these pages immediately compromises the account.
- Urgent Payment Requests: Attackers may impersonate suppliers or clients, requesting urgent payments via wire transfer or other methods. This creates pressure on the recipient to act quickly without verifying the request.
- Social Engineering Techniques: Sophisticated attackers use social engineering to increase the success rate of phishing attacks. This involves manipulating users' emotions or exploiting their trust to gain access to sensitive information. For example, an attacker might pose as a colleague or IT support staff.
Credential Stuffing and Brute-Force Attacks
Attackers often utilize stolen credentials obtained from other data breaches to attempt access to Office365 accounts. This method, known as credential stuffing, leverages lists of usernames and passwords leaked from other compromised systems.
- Credential Stuffing: Attackers use automated tools to try these stolen credentials against various online services, including Office365.
- Brute-Force Attacks: If credential stuffing fails, attackers may resort to brute-force attacks, where they systematically try numerous password combinations until they find the correct one. This is particularly effective against weak or easily guessable passwords.
- Importance of Strong Passwords and MFA: Implementing strong, unique passwords and multi-factor authentication (MFA) is crucial in mitigating the risks of credential stuffing and brute-force attacks. MFA adds an additional layer of security, requiring users to verify their identity through a second factor, such as a code from a mobile app or a security key.
Exploiting Vulnerabilities in Third-Party Apps
Attackers can exploit vulnerabilities in third-party applications integrated with Office365. These apps often have access to sensitive data, making them attractive targets.
- Vulnerable Apps: Out-of-date or poorly secured third-party apps can create entry points for attackers.
- Regular App Reviews and Updates: Regularly reviewing and updating third-party apps is crucial to patching vulnerabilities and minimizing risks.
- App Vetting: Before granting access to Office365 data, organizations should thoroughly vet third-party apps to ensure they meet security standards.
The Devastating Consequences of Office365 Breaches
The consequences of successful Office365 email compromise attacks can be severe and far-reaching.
Financial Losses
Federal authorities have reported millions of dollars in losses due to Office365 breaches. These financial impacts affect businesses of all sizes.
- Direct Financial Losses: Direct financial losses include funds stolen through fraudulent wire transfers or payments.
- Reputational Damage: Data breaches can severely damage an organization's reputation, leading to loss of customer trust and business.
- Legal Ramifications: Companies may face legal repercussions, including fines and lawsuits, due to non-compliance with data privacy regulations like GDPR and CCPA.
Data Breaches and Intellectual Property Theft
Compromised Office365 accounts can lead to significant data breaches, exposing sensitive information.
- Sensitive Data Exposure: This includes customer information, financial records, intellectual property, and confidential business communications.
- Compliance and Regulatory Implications: Data breaches can result in hefty fines and legal penalties under regulations like GDPR and CCPA.
- Long-Term Costs: Recovering from a data breach involves substantial costs, including forensic investigations, legal fees, and remediation efforts.
Operational Disruption
Compromised accounts can severely disrupt business operations.
- Email Spam and Malware Distribution: Attackers may use compromised accounts to send spam emails or distribute malware.
- Account Recovery Difficulties: Restoring compromised accounts and regaining control can be time-consuming and complex.
- Loss of Productivity: Disruption caused by security incidents leads to reduced productivity and loss of valuable working hours.
Protecting Your Organization from Office365 Email Compromise
Protecting your organization requires a multi-layered approach to security.
Implement Strong Password Policies and MFA
Strong password policies and multi-factor authentication are fundamental to Office365 security.
- Strong, Unique Passwords: Enforce the use of strong, unique passwords for all accounts.
- Password Managers: Recommend using password managers to securely store and manage passwords.
- Regular Password Rotations: Implement regular password rotation policies to minimize the impact of potential breaches.
- Multi-Factor Authentication (MFA): Mandate MFA for all Office365 users to add an extra layer of security.
Security Awareness Training for Employees
Educating employees about phishing and other cyber threats is crucial.
- Regular Training Programs: Conduct regular security awareness training programs to educate employees on identifying and avoiding phishing attempts.
- Identifying Suspicious Emails and Links: Train employees to recognize suspicious emails, links, and attachments.
- Phishing Simulations: Conduct regular phishing simulations to test employees' awareness and response.
Utilize Advanced Security Features in Office365
Leverage Office365's built-in security features.
- Advanced Threat Protection (ATP): Utilize ATP to detect and block malicious emails and attachments.
- Data Loss Prevention (DLP): Implement DLP policies to prevent sensitive data from leaving the organization.
- Microsoft Defender for Office 365: Deploy Microsoft Defender for Office 365 for comprehensive threat protection.
Regularly Review and Update Third-Party Apps
Regularly review and update third-party apps integrated with Office365.
- Robust App Approval Process: Establish a formal process for vetting and approving third-party applications.
- Monitor App Permissions: Regularly monitor and review the permissions granted to third-party apps.
- Regular Updates: Ensure all third-party apps are regularly updated to address security vulnerabilities.
Conclusion
The rise in Office365 email compromise schemes represents a significant threat to businesses of all sizes. Millions have already been lost, underscoring the critical need for proactive security measures. By implementing strong password policies, providing comprehensive security awareness training, utilizing advanced security features within Office365, and diligently managing third-party apps, organizations can significantly reduce their vulnerability to these devastating attacks. Don't wait until it's too late—take immediate action to protect your organization from the devastating consequences of an Office365 email compromise. Learn more about bolstering your Office365 security and mitigating the risk of an Office365 email compromise today!

Featured Posts
-
 O Gallos Ypoyrgos Oikonomias Zita Patriotismo Apenanti Stoys Dasmoys Tramp
Apr 30, 2025
O Gallos Ypoyrgos Oikonomias Zita Patriotismo Apenanti Stoys Dasmoys Tramp
Apr 30, 2025 -
 Strategys 555 8 Million Bitcoin Acquisition Key Details And Implications
Apr 30, 2025
Strategys 555 8 Million Bitcoin Acquisition Key Details And Implications
Apr 30, 2025 -
 German Conservatives And Social Democrats Begin Coalition Talks
Apr 30, 2025
German Conservatives And Social Democrats Begin Coalition Talks
Apr 30, 2025 -
 Top New Cruise Ships Launching In 2025 A Comprehensive Guide
Apr 30, 2025
Top New Cruise Ships Launching In 2025 A Comprehensive Guide
Apr 30, 2025 -
 Watch Live Ru Pauls Drag Race Live Reaches 1 000 Performances
Apr 30, 2025
Watch Live Ru Pauls Drag Race Live Reaches 1 000 Performances
Apr 30, 2025
Latest Posts
-
 The X Files Duo Gillian Anderson And David Duchovnys Sag Awards Moment
Apr 30, 2025
The X Files Duo Gillian Anderson And David Duchovnys Sag Awards Moment
Apr 30, 2025 -
 Ben Afflecks New Movie Features A Gripping Shootout With Gillian Anderson
Apr 30, 2025
Ben Afflecks New Movie Features A Gripping Shootout With Gillian Anderson
Apr 30, 2025 -
 Uk Eurovision 2024 Analysing Remember Mondays Anti Cyberbullying Anthem
Apr 30, 2025
Uk Eurovision 2024 Analysing Remember Mondays Anti Cyberbullying Anthem
Apr 30, 2025 -
 Tiesa Anapus Ekrano X Failu Aktoriu Gyvenimai
Apr 30, 2025
Tiesa Anapus Ekrano X Failu Aktoriu Gyvenimai
Apr 30, 2025 -
 On Set Ben Affleck And Gillian Anderson Film Action Packed Scene
Apr 30, 2025
On Set Ben Affleck And Gillian Anderson Film Action Packed Scene
Apr 30, 2025
