Federal Investigation: Hacker Exploits Office365 To Steal Millions

Table of Contents
The Sophisticated Office365 Phishing Campaign
The perpetrators employed a highly sophisticated phishing campaign to gain unauthorized access to the victim's Office365 environment. This wasn't a simple, mass-sent spam email; instead, it was a targeted attack leveraging several advanced techniques. The hackers used a combination of spear phishing, email spoofing, and potentially credential stuffing to bypass security measures.
- Spear Phishing: Emails were meticulously crafted to target specific individuals within the organization, leveraging publicly available information to personalize the message and increase the chances of success.
- Email Spoofing: The attackers cleverly mimicked legitimate sender addresses, making the emails appear to originate from trusted sources within the company or from known business partners.
- Credential Stuffing: Stolen credentials from previous data breaches may have been used to attempt logins, exploiting weaknesses in password management.
Key characteristics of the phishing emails included:
- Use of legitimate-looking sender addresses (e.g., mimicking internal email addresses or those of trusted vendors).
- Urgent or emotionally manipulative subject lines designed to create a sense of urgency and pressure recipients into immediate action.
- Links to convincing fake login pages, almost indistinguishable from the real Office365 login portal, designed to steal user credentials.
The Data Breach and its Extent
The breach resulted in the theft of a significant amount of sensitive data, including financial records, confidential employee information, and potentially valuable intellectual property. The exact number of compromised accounts remains under investigation, but initial estimates suggest hundreds of accounts were affected, leading to an estimated multi-million dollar financial loss.
The consequences of this breach are far-reaching:
- Significant Financial Losses: The direct financial impact on the victimized company is substantial, including the cost of remediation, legal fees, and potential regulatory fines.
- Legal Repercussions: The company faces potential legal action from affected employees, customers, and regulatory bodies.
- Reputational Damage: The breach has severely damaged the company's reputation and trust among its stakeholders. This can lead to long-term financial implications.
The Federal Investigation and its Progress
Federal agencies, including the FBI, are actively involved in the Federal Investigation Office365 Breach. The investigation involves a complex process of tracing the hacker's digital footprint, analyzing stolen data, and collaborating with international agencies if the perpetrators are located overseas. While no arrests have been publicly announced yet, the investigation is ongoing, and the potential charges against the perpetrators could include wire fraud, identity theft, and computer hacking.
The investigative process involves several key steps:
- Tracing the Hacker's Digital Footprint: Investigators are meticulously tracking the hacker's online activity to identify their location, methods, and potential accomplices.
- Collaboration with International Agencies: If the investigation leads overseas, collaboration with international law enforcement agencies is crucial.
- Analysis of Stolen Data: Forensic analysis of the stolen data is essential to determine the full extent of the breach and identify any potential vulnerabilities.
Lessons Learned and Best Practices for Office365 Security
This incident underscores the critical need for robust Office365 security measures. Preventing future breaches requires a multi-pronged approach:
- Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security, making it significantly harder for attackers to access accounts even if they obtain credentials.
- Employee Security Awareness Training: Regular training programs are crucial to educate employees about phishing scams and other social engineering techniques.
- Regular Security Audits: Conduct regular security assessments to identify and address potential vulnerabilities in your Office365 environment.
Implementing the following preventative measures is also vital:
- Regular security audits to identify and mitigate vulnerabilities.
- Strong password policies and password management tools.
- Implementing advanced threat protection features offered by Office365.
- Using robust email security gateways to filter out malicious emails.
Protecting Your Business from Federal Investigation Office365 Breaches
The severity of this Federal Investigation Office365 Breach highlights the critical need for proactive cybersecurity measures. The sophisticated nature of this attack emphasizes that relying solely on default security settings is insufficient. Organizations must actively invest in comprehensive security solutions and employee training to protect themselves.
To avoid becoming the next victim of a similar incident, immediately assess your Office365 security posture. Implement multi-factor authentication, conduct regular security audits, and invest in comprehensive cybersecurity training for your employees. Consider seeking professional assistance for an Office365 security audit and implementing advanced threat protection to strengthen your defenses. Remember, proactive measures are key to preventing costly Office365 data breaches and avoiding a potential Federal Investigation Office365 Breach. For more information on cybersecurity best practices and enhancing your Office365 security, explore resources from Microsoft and reputable cybersecurity firms.

Featured Posts
-
 Bmw And Porsches China Challenges A Growing Trend In The Auto Industry
Apr 23, 2025
Bmw And Porsches China Challenges A Growing Trend In The Auto Industry
Apr 23, 2025 -
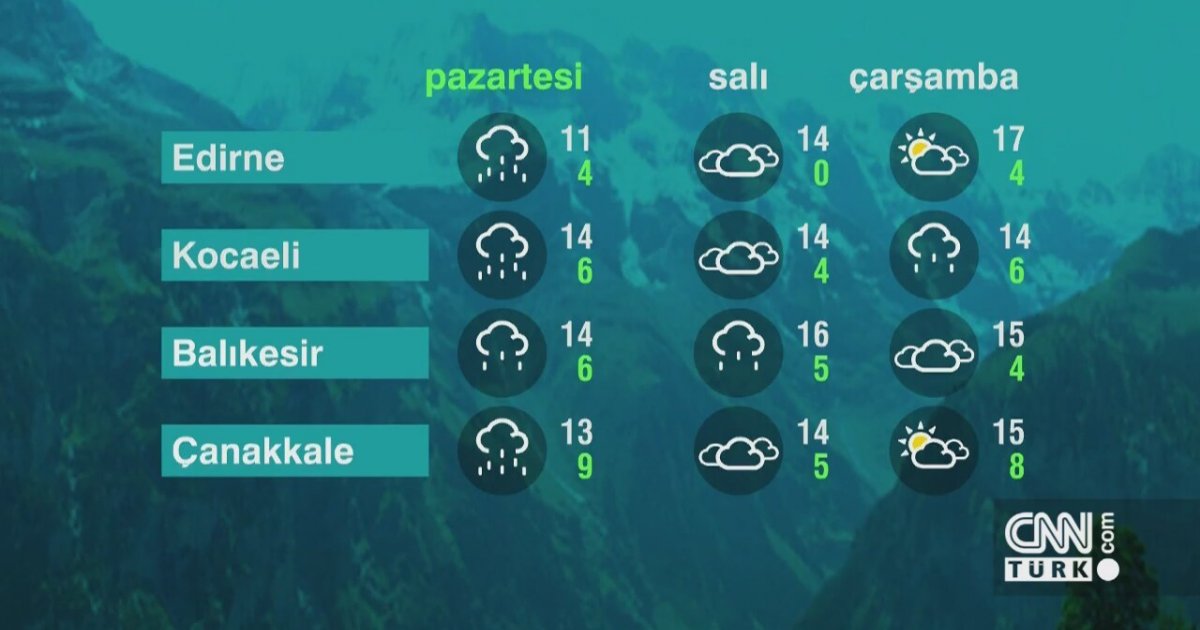 Izmir Okul Tatil Karari 24 Subat Pazartesi Icin Son Durum Ve Aciklama
Apr 23, 2025
Izmir Okul Tatil Karari 24 Subat Pazartesi Icin Son Durum Ve Aciklama
Apr 23, 2025 -
 Bank Of Canadas Rate Pause Expert Analysis From Fp Video
Apr 23, 2025
Bank Of Canadas Rate Pause Expert Analysis From Fp Video
Apr 23, 2025 -
 Bu Aksamki Diziler 7 Nisan Pazartesi
Apr 23, 2025
Bu Aksamki Diziler 7 Nisan Pazartesi
Apr 23, 2025 -
 The Post Roe Landscape Examining The Role Of Over The Counter Birth Control
Apr 23, 2025
The Post Roe Landscape Examining The Role Of Over The Counter Birth Control
Apr 23, 2025
Latest Posts
-
 Abcs Programming Strategy Re Airing High Potential Episodes In March 2025
May 10, 2025
Abcs Programming Strategy Re Airing High Potential Episodes In March 2025
May 10, 2025 -
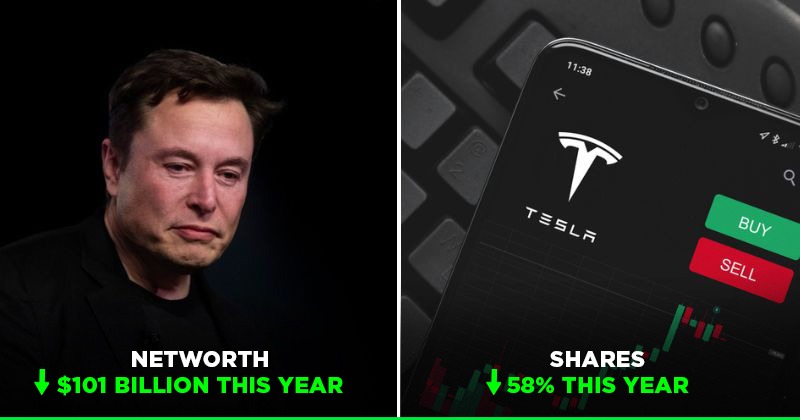 Tesla Stock Decline Pushes Elon Musks Net Worth Below 300 Billion Mark
May 10, 2025
Tesla Stock Decline Pushes Elon Musks Net Worth Below 300 Billion Mark
May 10, 2025 -
 Official Madhyamik Result 2025 And Merit List Website
May 10, 2025
Official Madhyamik Result 2025 And Merit List Website
May 10, 2025 -
 Tech Billionaires 194 Billion Loss A 100 Day Analysis Of Trump Inauguration Donors
May 10, 2025
Tech Billionaires 194 Billion Loss A 100 Day Analysis Of Trump Inauguration Donors
May 10, 2025 -
 Madhyamik 2025 Expected Merit List And Cut Off Marks
May 10, 2025
Madhyamik 2025 Expected Merit List And Cut Off Marks
May 10, 2025
