How North Korean Actors Exploit US Remote Workers

Table of Contents
The Methods Employed by North Korean Actors
North Korean actors utilize a range of techniques to compromise remote US workers, leveraging both technical prowess and social engineering skills. These methods are often combined for maximum impact, making detection and prevention more challenging.
Phishing and Social Engineering Tactics
Phishing remains a highly effective attack vector. North Korean actors craft deceptively realistic emails mimicking legitimate communications. Common tactics include:
- Fake invoices: Emails appear to be from vendors, demanding urgent payment with embedded malware.
- Urgent requests: Emails impersonate supervisors or colleagues, requesting immediate action (e.g., accessing a file, changing a password) that leads to malware infection.
- Employment opportunities: These lure unsuspecting individuals with promises of high-paying jobs, often leading to the installation of malicious software or the disclosure of personal information.
Social engineering goes beyond email. Attackers might impersonate IT support, requesting remote access to troubleshoot a problem. They might even call, posing as a superior, seeking confidential information. These tactics prey on human psychology, manipulating individuals into compromising security protocols.
Malware and Ransomware Deployment
Once initial access is gained, North Korean actors deploy various forms of malware, including:
- Data stealers: These tools exfiltrate sensitive data like financial records, intellectual property, and customer information.
- Ransomware: This encrypts files, rendering them inaccessible unless a ransom is paid in cryptocurrency. Ransomware attacks can cripple businesses and cause significant financial losses.
- Advanced Persistent Threats (APTs): These sophisticated attacks involve long-term, stealthy intrusion to gain access to high-value targets, remaining undetected for extended periods.
The impact of ransomware attacks on remote workers extends beyond the loss of data. It can disrupt operations, damage reputation, and lead to significant legal and financial repercussions for both the employee and the employer.
Exploiting Remote Access Software Vulnerabilities
Remote access software, such as VPNs and RDP (Remote Desktop Protocol), are essential for remote work, but they are also potential vulnerabilities. North Korean hackers exploit known security flaws in these tools to gain unauthorized access to corporate networks. This provides them with a foothold to move laterally, accessing sensitive data and systems.
The Targets and Objectives of North Korean Cyberattacks
While various remote workers are vulnerable, those with access to sensitive information are prime targets. This includes:
- Individuals in finance, handling sensitive financial data and transactions.
- Employees in research and development, possessing valuable intellectual property.
- Government employees, holding access to classified information.
The objectives behind these attacks are multifaceted:
Financial Gain
The primary motivation is often financial profit. North Korean actors seek to steal money, cryptocurrency, and intellectual property for resale on the dark web. This illicit activity generates revenue for the regime.
Geopolitical Espionage
Cyberattacks also serve geopolitical objectives. Stealing sensitive government or corporate data provides strategic advantages, aiding in espionage and potentially disrupting US interests.
Protecting Yourself from North Korean Cyberattacks
Protecting yourself from these sophisticated attacks requires a multi-layered approach:
Strong Passwords and Multi-Factor Authentication (MFA)
Employ strong, unique passwords for every account and enable MFA wherever possible. This adds an extra layer of security, significantly reducing the risk of unauthorized access.
Regular Software Updates and Patching
Keep all software, including operating systems, applications, and remote access tools, up-to-date with the latest security patches. This mitigates known vulnerabilities exploited by attackers.
Cybersecurity Awareness Training
Participate in regular cybersecurity awareness training to learn how to identify and avoid phishing attempts, social engineering tactics, and other cyber threats.
Reporting Suspicious Activity
Report any suspicious emails, links, or files immediately to your IT or security personnel. Timely reporting is crucial in containing potential breaches.
The Role of Government and Private Sector Collaboration
Combating North Korean cyber threats requires collaboration between government agencies, such as the Cybersecurity and Infrastructure Security Agency (CISA), and private sector cybersecurity firms. Information sharing and threat intelligence are vital for effective defense. Joint efforts in developing advanced detection and response capabilities are crucial in mitigating these attacks.
Conclusion: Staying Safe from North Korean Cyber Exploitation of Remote Workers
North Korean state-sponsored actors pose a significant threat to US remote workers, employing diverse techniques to steal data and disrupt operations. Safeguarding your remote workforce requires a proactive approach, incorporating robust security measures at both individual and organizational levels. By strengthening passwords, enabling MFA, regularly patching software, undergoing cybersecurity training, and promptly reporting suspicious activities, you can significantly reduce your vulnerability. Preventing North Korean cyber exploitation necessitates a collective effort, involving collaboration between government and private sectors. Improving your remote worker cybersecurity should be a top priority. Take immediate action to protect yourself and your organization from these dangerous attacks.

Featured Posts
-
 Nike Sneakers May 2025 Release Calendar Your Essential Buying Guide
May 29, 2025
Nike Sneakers May 2025 Release Calendar Your Essential Buying Guide
May 29, 2025 -
 Trumps Trade War Wall Street Bets On A Brighter Future
May 29, 2025
Trumps Trade War Wall Street Bets On A Brighter Future
May 29, 2025 -
 Jamie Foxxs All Star Weekend Robert Downey Jr S Hispanic Role
May 29, 2025
Jamie Foxxs All Star Weekend Robert Downey Jr S Hispanic Role
May 29, 2025 -
 Razgatlioglu Sets The Record Straight On Moto Gp Rumors
May 29, 2025
Razgatlioglu Sets The Record Straight On Moto Gp Rumors
May 29, 2025 -
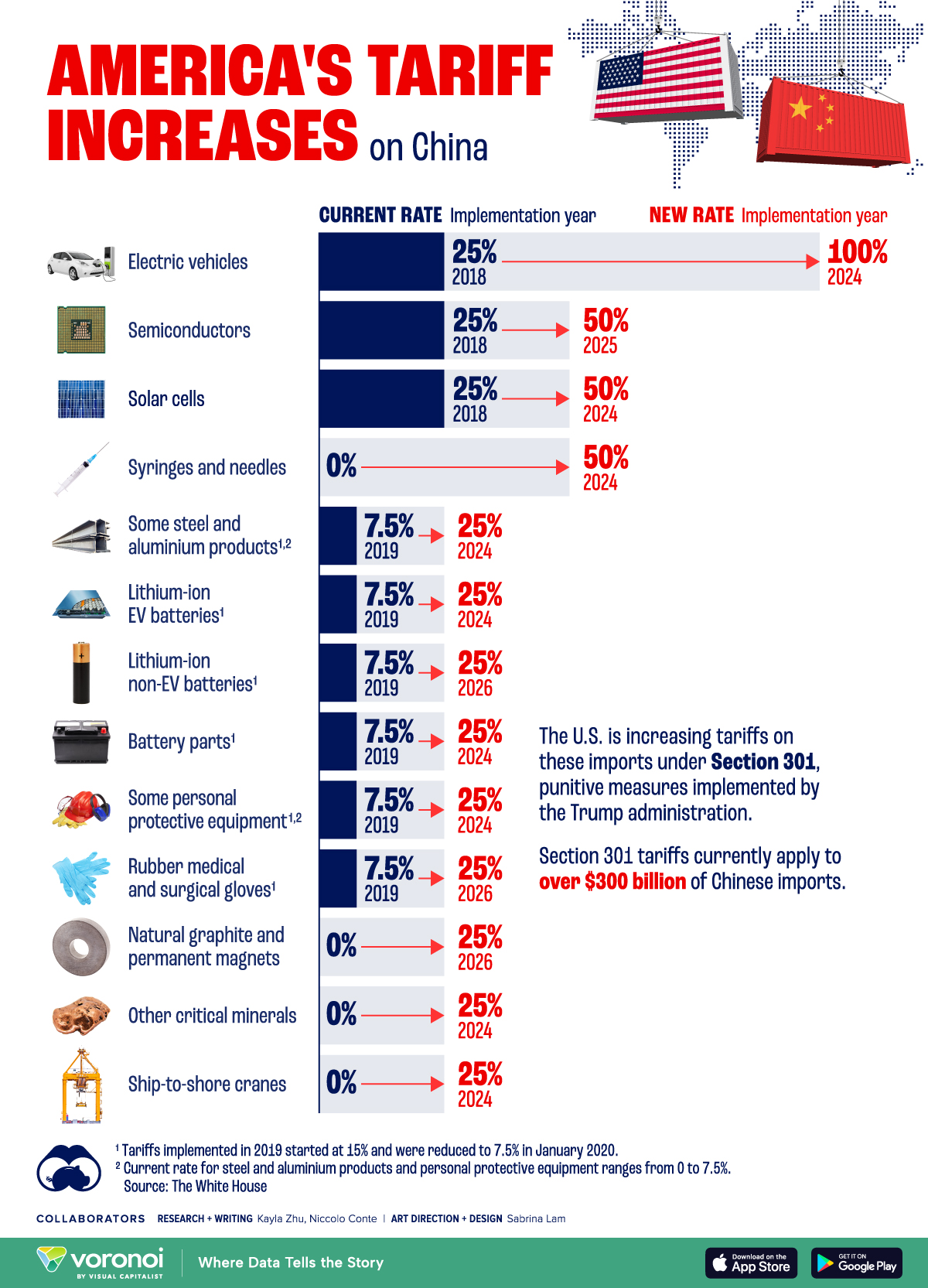 Impact Of Tariffs On Canadian Businesses Uncertainty And Economic Outlook Stat Can
May 29, 2025
Impact Of Tariffs On Canadian Businesses Uncertainty And Economic Outlook Stat Can
May 29, 2025
Latest Posts
-
 Estevan Street Sweeping Schedule 2024 Full Dates Released
May 31, 2025
Estevan Street Sweeping Schedule 2024 Full Dates Released
May 31, 2025 -
 The Good Life And You A Personalized Approach To Happiness
May 31, 2025
The Good Life And You A Personalized Approach To Happiness
May 31, 2025 -
 Rosemary And Thyme History Folklore And Culinary Traditions
May 31, 2025
Rosemary And Thyme History Folklore And Culinary Traditions
May 31, 2025 -
 Pursuing The Good Life A Holistic Approach
May 31, 2025
Pursuing The Good Life A Holistic Approach
May 31, 2025 -
 What Is The Good Life Exploring Personal Definitions And Paths
May 31, 2025
What Is The Good Life Exploring Personal Definitions And Paths
May 31, 2025
