Office365 Breach Nets Millions: Insider Reveals Details Of Executive Targeting

Table of Contents
The Scale of the Office365 Breach and Financial Impact
The recent Office365 breach represents a significant security failure, resulting in substantial financial losses for multiple organizations. While precise figures remain confidential due to ongoing investigations, sources suggest the total financial impact runs into the millions of dollars. This encompasses direct losses from stolen intellectual property, financial data breaches, and the costs associated with responding to the incident, including legal fees and regulatory fines. The breach also affected a significant number of executives across several companies, highlighting the attackers' strategic targeting.
- Quantifiable financial losses: Estimates place the losses in the multi-million dollar range, impacting both revenue and operational efficiency.
- Specific examples of stolen data: While specifics are limited to protect ongoing investigations, reports indicate the theft of sensitive financial information, strategic business plans, and confidential client data.
- Legal repercussions and regulatory fines: Companies affected face potential legal repercussions and hefty fines due to non-compliance with data protection regulations such as GDPR and CCPA. The reputational damage alone can cost millions. This Office365 security incident underscores the financial and legal risks associated with inadequate cybersecurity measures.
Insider's Account: Tactics Used in the Office365 Targeted Attack
An insider's account reveals the sophisticated tactics employed in this targeted Office365 attack. The attackers primarily leveraged spear-phishing campaigns, crafting highly personalized emails designed to bypass basic spam filters and deceive unsuspecting executives. These emails contained malicious attachments or links leading to credential-harvesting websites or exploiting zero-day vulnerabilities in Office365 applications.
- Step-by-step breakdown of the attack process: The attack started with highly targeted spear-phishing emails. Once an executive clicked a malicious link or opened an infected attachment, the attackers gained access to their Office365 accounts. This provided a foothold for lateral movement within the organization's network. From there, they exfiltrated data and installed ransomware.
- Highlighting the sophistication of the techniques employed: The attackers demonstrated a high level of sophistication, utilizing advanced techniques like credential stuffing, combined with social engineering tactics to maximize their chances of success. Their understanding of executive routines and communication patterns allowed them to craft highly believable phishing emails.
- Mention of specific vulnerabilities exploited in Office365: While specific vulnerabilities are not publicly disclosed to prevent further exploitation, it's likely that the attackers leveraged known and unknown vulnerabilities in Office365 applications and services. This highlights the importance of continuous patching and updates.
Vulnerabilities Exploited in Office365 and Mitigation Strategies
The Office365 breach exposed several critical vulnerabilities, including weak passwords and a lack of multi-factor authentication (MFA). These weaknesses allowed the attackers to easily compromise accounts and gain access to sensitive data. The attackers also exploited vulnerabilities in older versions of Office365 applications and neglected security updates.
- Recommendations for strong password policies and MFA implementation: Implementing strong password policies with enforced password complexity and regular password changes is paramount. Crucially, multi-factor authentication (MFA) should be mandatory for all users, especially executives.
- Importance of regular security audits and vulnerability scans: Regular security audits and penetration testing are essential for identifying and addressing vulnerabilities before attackers can exploit them. These audits should specifically assess the security posture of Office365 and integrated applications.
- Use of advanced threat protection and email security solutions: Investing in robust email security solutions, including advanced threat protection and anti-phishing measures, is crucial to identify and block malicious emails before they reach users' inboxes.
Lessons Learned and Best Practices for Office365 Security
This Office365 breach underscores the critical need for proactive security measures and employee training. Relying solely on reactive responses is no longer sufficient.
- Investing in robust security awareness training programs for employees: Regular security awareness training is essential to educate employees about phishing scams, social engineering tactics, and safe internet practices.
- Regularly updating Office365 security settings and patches: Staying up-to-date with the latest Office365 security patches and updates is crucial to address known vulnerabilities. This includes promptly implementing all security updates provided by Microsoft.
- Implementing advanced threat protection and data loss prevention (DLP) measures: Advanced threat protection solutions, along with robust data loss prevention (DLP) measures, can significantly reduce the risk of data breaches and minimize the impact of successful attacks.
Conclusion
The Office365 breach highlighted the critical need for robust security measures to protect against targeted attacks aimed at executives. The insider's account revealed sophisticated techniques, emphasizing the importance of proactive security strategies. Don't become the next victim of an Office365 breach. Implement strong security measures, including multi-factor authentication, regular security audits, and employee training, to safeguard your organization against costly and reputation-damaging Office365 security incidents. Learn more about protecting your business from Office365 breaches today!

Featured Posts
-
 Inside The Mansions Mtv Cribs And The World Of Rich Kids
May 12, 2025
Inside The Mansions Mtv Cribs And The World Of Rich Kids
May 12, 2025 -
 How Apples Decisions Impact Googles Competitive Landscape
May 12, 2025
How Apples Decisions Impact Googles Competitive Landscape
May 12, 2025 -
 Ufc 315 Main Event Muhammad Vs Della Maddalena Fight Recap And Scores
May 12, 2025
Ufc 315 Main Event Muhammad Vs Della Maddalena Fight Recap And Scores
May 12, 2025 -
 Lily Collins Stars In Sexy Calvin Klein Campaign See Photo 5133601
May 12, 2025
Lily Collins Stars In Sexy Calvin Klein Campaign See Photo 5133601
May 12, 2025 -
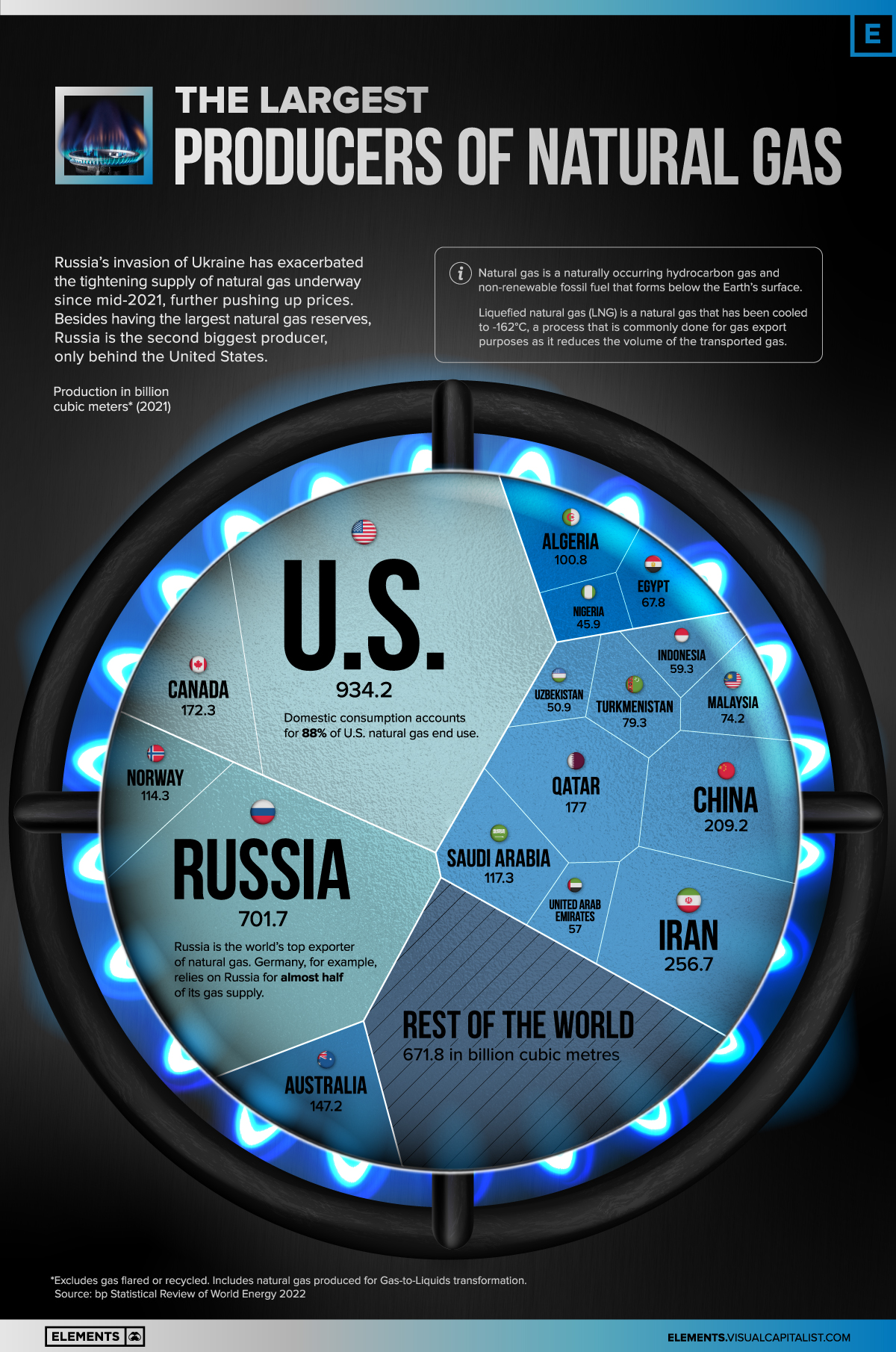 Growth Of Canadas Leading Natural Gas Producer Market Dominance And Future Prospects
May 12, 2025
Growth Of Canadas Leading Natural Gas Producer Market Dominance And Future Prospects
May 12, 2025
Latest Posts
-
 The Vma Simulcast On Cbs A Death Knell For Mtv
May 12, 2025
The Vma Simulcast On Cbs A Death Knell For Mtv
May 12, 2025 -
 Mtv Vs Cbs Did The Vma Simulcast Signal Mtvs Decline
May 12, 2025
Mtv Vs Cbs Did The Vma Simulcast Signal Mtvs Decline
May 12, 2025 -
 Is The Cbs Vma Simulcast The Final Nail In Mtvs Coffin
May 12, 2025
Is The Cbs Vma Simulcast The Final Nail In Mtvs Coffin
May 12, 2025 -
 Mtv Cribs The Ultimate Guide To Rich Kids Real Estate
May 12, 2025
Mtv Cribs The Ultimate Guide To Rich Kids Real Estate
May 12, 2025 -
 Rich Kids Cribs A Tour Of Lavish Homes On Mtv Cribs
May 12, 2025
Rich Kids Cribs A Tour Of Lavish Homes On Mtv Cribs
May 12, 2025
