Millions Stolen Via Office365: Federal Investigation Into Executive Email Compromise
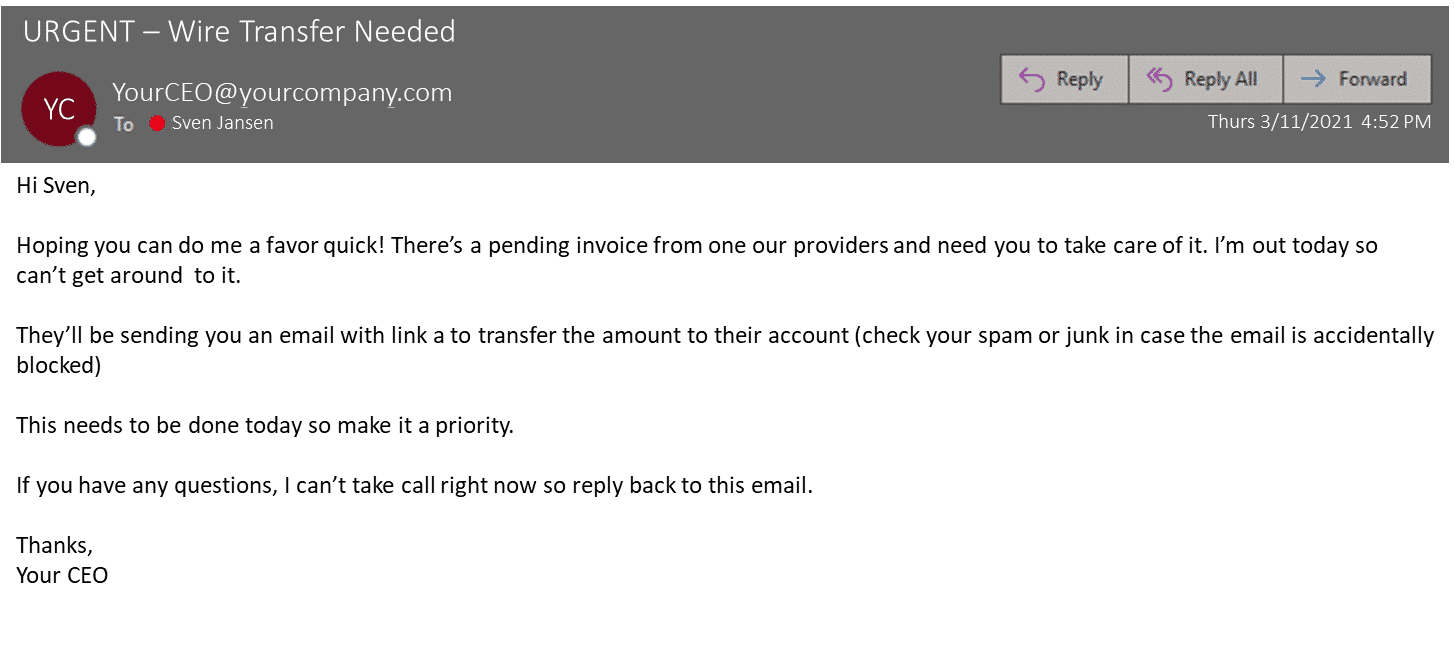
Table of Contents
The Modus Operandi: How Cybercriminals Compromised Office365 Accounts
Cybercriminals employ sophisticated techniques to breach Office365 accounts, often targeting executives who have access to sensitive financial information. Their methods are constantly evolving, requiring businesses to stay vigilant and adapt their security protocols.
-
Phishing Attacks and Spear Phishing: Attackers frequently use phishing emails disguised as legitimate communications from trusted sources. Spear phishing takes this a step further, targeting specific individuals with highly personalized emails designed to trick them into revealing login credentials or downloading malware. These emails may mimic internal communications or invoices, appearing convincingly authentic.
-
Malware and Credential Theft: Once an initial foothold is gained, attackers often deploy malware to steal credentials, gain persistent access, and exfiltrate sensitive data. This malware can range from keyloggers capturing keystrokes to more sophisticated tools that move laterally within a network, compromising additional accounts and systems.
-
Multi-Factor Authentication (MFA) Bypass: While MFA significantly enhances security, determined attackers are constantly seeking ways to circumvent it. Techniques include phishing for one-time codes, exploiting vulnerabilities in MFA systems, or using stolen or compromised devices. Therefore, robust MFA implementation and employee training are crucial.
-
Maintaining Persistent Access: Successfully bypassing security measures is only half the battle. Attackers often strive to maintain persistent access to compromised accounts. This allows them to conduct their malicious activities undetected for extended periods, often extracting data gradually to avoid detection. This highlights the critical need for robust monitoring and threat detection systems.
The Financial Fallout: The Scale of the Office365 Data Breach and its Impact
The financial consequences of a successful Office365 compromise can be devastating. The federal investigation revealed losses amounting to millions of dollars for affected organizations.
-
Financial Losses: The direct financial impact includes the stolen funds themselves, but also extends to the costs of forensic investigation, legal fees, regulatory fines, and reputational damage repair. The loss of intellectual property or sensitive customer data can also have long-term financial repercussions.
-
Data Theft: Stolen data can include anything from financial records and bank account details to sensitive customer information, intellectual property, and strategic business plans. This information can be sold on the dark web, used for further attacks, or leveraged for corporate espionage.
-
Reputational Damage: A data breach, particularly one involving executive email compromise, can severely damage an organization's reputation, leading to loss of customer trust, decreased investor confidence, and potential negative media coverage. The long-term effects on brand image and market standing can be significant.
-
Legal and Regulatory Consequences: Organizations facing a data breach must navigate complex legal and regulatory frameworks like GDPR and CCPA. Failure to comply with these regulations can result in substantial fines and legal action. Insurance claims may also be impacted by the organization's response to and preparedness for the breach.
The Federal Investigation: Key Findings and Implications for Businesses
The federal investigation highlighted critical vulnerabilities in many organizations’ cybersecurity posture. The findings underscore the need for proactive measures to protect against Office365 compromise and other forms of cybercrime.
-
Key Findings: The investigation likely uncovered specific vulnerabilities exploited by the attackers, shedding light on common weaknesses in email security practices, MFA implementation, and employee training programs.
-
Implications for Businesses: The findings emphasize the need for a comprehensive cybersecurity strategy that goes beyond basic security measures. This includes proactive threat detection, incident response planning, and employee training.
-
Regulatory Compliance: Compliance with data protection regulations, such as GDPR and CCPA, is no longer optional but mandatory. Organizations must ensure their data handling practices adhere to these stringent regulations to avoid severe penalties.
-
Data Breach Response Plan: Having a well-defined and regularly tested data breach response plan is crucial. This plan should outline the steps to be taken in the event of a breach, from initial detection to containment, investigation, and remediation.
Strengthening Office365 Security: Practical Steps to Prevent Executive Email Compromise
Protecting your organization from Office365 compromise requires a multi-layered approach that combines technological solutions with robust security awareness training.
-
Multi-Factor Authentication (MFA): Enforce strong MFA for all Office365 accounts. This adds an extra layer of security, making it significantly more difficult for attackers to gain unauthorized access even if they obtain passwords.
-
Security Awareness Training: Regular and engaging security awareness training is paramount. Educate employees about phishing techniques, malware threats, and the importance of reporting suspicious emails. Simulate phishing attacks to test employee awareness and reinforce training.
-
Advanced Threat Protection: Implement advanced threat protection tools that leverage AI and machine learning to detect and block sophisticated threats, including spear phishing and malware. These solutions offer real-time protection against evolving threats.
-
Email Filtering and Security: Utilize robust email filtering and security solutions to identify and quarantine malicious emails before they reach employee inboxes. Regularly update your email security settings and filters to stay ahead of new threats. Consider employing email authentication protocols like DKIM, SPF, and DMARC to further enhance email security.
Conclusion
The federal investigation into the millions stolen via compromised Office365 accounts serves as a stark warning to organizations of all sizes. Executive email compromise poses a significant threat, capable of inflicting substantial financial and reputational damage. By implementing robust security measures, including strong MFA, comprehensive security awareness training, and advanced threat protection, businesses can significantly reduce their vulnerability to these sophisticated attacks. Proactive steps to enhance email security and overall cybersecurity are crucial for protecting your organization from the devastating consequences of a data breach.
Call to Action: Don't become another statistic. Protect your organization from the devastating consequences of Office365 compromise. Implement strong email security measures today to safeguard your data and financial assets. Learn more about securing your Office365 environment and preventing executive email compromise. Invest in robust cybersecurity solutions and employee training to mitigate the risk of BEC and other email-based threats.

Featured Posts
-
 Rep Jasmine Crockett On Trumps Economic Policies Grocery Prices And Wages Under Attack
May 17, 2025
Rep Jasmine Crockett On Trumps Economic Policies Grocery Prices And Wages Under Attack
May 17, 2025 -
 Repetitive Documents An Ai Solution For Creating A Poop Podcast
May 17, 2025
Repetitive Documents An Ai Solution For Creating A Poop Podcast
May 17, 2025 -
 New York Daily News Back Pages May 2025 Archive
May 17, 2025
New York Daily News Back Pages May 2025 Archive
May 17, 2025 -
 Japans Gdp Decline In First Quarter Trump Tariffs Loom
May 17, 2025
Japans Gdp Decline In First Quarter Trump Tariffs Loom
May 17, 2025 -
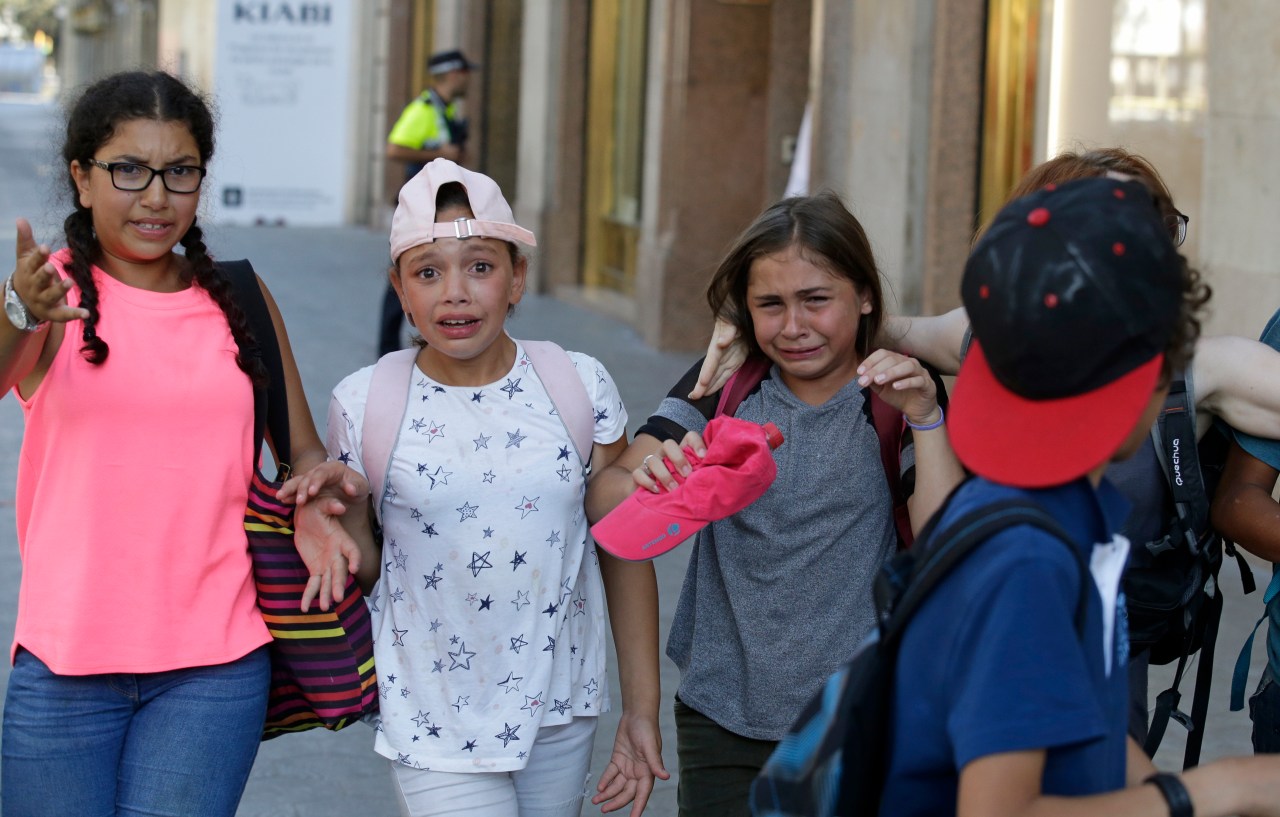 13 Injured After Car Plows Into Crowd Outside Barcelona Football Match
May 17, 2025
13 Injured After Car Plows Into Crowd Outside Barcelona Football Match
May 17, 2025
Latest Posts
-
 Trumps Student Loan Executive Order The Black Community Responds
May 17, 2025
Trumps Student Loan Executive Order The Black Community Responds
May 17, 2025 -
 Black Americans Reactions To Trumps Student Loan Plan
May 17, 2025
Black Americans Reactions To Trumps Student Loan Plan
May 17, 2025 -
 How Student Loan Debt Impacts Your Ability To Buy A House
May 17, 2025
How Student Loan Debt Impacts Your Ability To Buy A House
May 17, 2025 -
 Buying A House How Student Loans Affect Your Mortgage
May 17, 2025
Buying A House How Student Loans Affect Your Mortgage
May 17, 2025 -
 The Ultimate Guide To Refinancing Federal Student Loans
May 17, 2025
The Ultimate Guide To Refinancing Federal Student Loans
May 17, 2025
